Security News
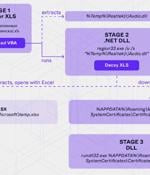
Opposition activists in Belarus as well as Ukrainian military and government organizations are the target of a new campaign that employs malware-laced Microsoft Excel documents as lures to deliver...

Forescout’s 2024H1 Threat Review is a new report that reviews the current state of vulnerabilities, threat actors, and ransomware attacks in the first half of 2024 and compares them to H1 2023....
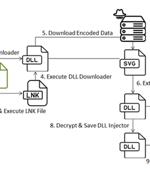
A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per...

The Bumblebee malware loader seemingly vanished from the internet last October, but it's back and - oddly - relying on a vintage vector to try and gain access. First spotted in 2022 by researchers at Proofpoint - who identified it as an apparent replacement for BazarLoader - Bumblebee was originally used by high-profile ransomware groups including Russia-linked Conti.

Xlam files are now the seventh most commonly abused file extension in Q3 2023, rising 35 places from 42nd on the list in Q2. XLL attacks aren't new and researchers observed a lull in exploits at the start of 2023, but a surge in attention has been given to them in the past few months. XLL files offer attackers greater capabilities compared to alternatives like Visual Basic for Applications macros, which are now blocked by default courtesy of Microsoft's 2022 intervention, a move that was seen at the time as long overdue.

"The shift to the cloud has been a long journey and attackers are taking advantage now that employees regularly log into multiple cloud services, often from outside the traditional enterprise network perimeter," said Ariel Tseitlin, Partner at Scale Venture Partners and an avid investor in the cloud and security industries. As AI/ML models become more commonplace within organizations, 49% of security leaders worried about threat actors poisoning those AI/ML models to bypass security protections.

Microsoft's decision to block internet-sourced macros by default last year is forcing attackers to find new and creative ways to compromise systems and deliver malware, according to threat researchers at Proofpoint. "Financially motivated threat actors that gain initial access via email are no longer using static, predictable attack chains, but rather dynamic, rapidly changing techniques."

The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. A derivative of the Cridex banking worm - which was subsequently replaced by Dridex around the same time GameOver Zeus was disrupted in 2014 - Emotet has evolved into a "Monetized platform for other threat actors to run malicious campaigns on a pay-per-install model, allowing theft of sensitive data and ransom extortion."
In a continuing sign that threat actors are adapting well to a post-macro world, it has emerged that the use of Microsoft OneNote documents to deliver malware via phishing attacks is on the rise. Enterprise firm Proofpoint said it detected over 50 campaigns leveraging OneNote attachments in the month of January 2023 alone.

Microsoft's move last year to block macros by default in Office applications is forcing miscreants to find other tools with which to launch cyberattacks, including the software vendor's LNK files - the shortcuts Windows uses to point to other files. The files are also helping criminals gain initial access into victims' systems before running such threats as the Qakbot backdoor malware, malware loader Bumblebee, and IcedID, a malware dropper, according to the Talos researchers.