Security News

A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple's on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection. The new iteration "Continues to impact Mac users who rely solely on Apple's built-in security control XProtect for malware detection," SentinelOne threat researcher Phil Stokes said in an analysis published last week.
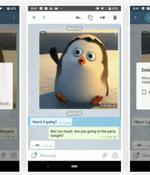
A vulnerability in a high-level privacy feature of Telegram on macOS that sets up a "Self-destruct" timer for messages on both the sender's and recipient's devices can allow someone to retrieve these messages even after they've been deleted, a researcher has found. Reegun Richard Jayapaul, Trustwave SpiderLabs Lead Threat Architect, discovered the flaw in the Self-Destruct feature of Telegram MacOS, which is part of the Secret-Chats aspect of the messaging app that uses end-to-end encryption.

Apple patched a zero-day flaw on Monday, found in both its iOS and macOS platforms that's being actively exploited in the wild and can allow attackers to take over an affected system. Apple released three updates, iOS 14.7., iPadOS 14.7.1 and macOS Big Sur 11.5.1 to patch the vulnerability on each of the platforms Monday.

The bug, CVE-2021-30807, was found in the iGiant's IOMobileFrameBuffer code, a kernel extension for managing the screen frame buffer that could be abused to run malicious code on the affected device. Apple did not say who might be involved in the exploitation of this bug.

A malware known for targeting macOS operating system has been updated once again to add more features to its toolset that allows it to amass and exfiltrate sensitive data stored in a variety of apps, including apps such as Google Chrome and Telegram, as part of further "Refinements in its tactics." Earlier this April, XCSSET received an upgrade that enabled the malware authors to target macOS 11 Big Sur as well as Macs running on M1 chipset by circumventing new security policies instituted by Apple in the latest operating system.

Security researchers have published details about the method used by a strain of macOS malware to steal login information from multiple apps, enabling its operators to steal accounts. Dubbed XCSSET, the malware keeps evolving and has been targeting macOS developers for more than a year by infecting local Xcode projects.

Cybersecurity researchers on Wednesday disclosed details of an evolving malware that has now been upgraded to steal sensitive information from Apple's macOS operating system. While the very first Formbook samples were detected in the wild in January 2016, the sale of the malware on underground forums stopped in October 2017, only to be resurrected more than two years later in the form of XLoader in February 2020.

A highly popular malware for stealing information from Windows systems has been modified into a new strain called XLoader, which can also target macOS systems. The connection between the two malware pieces was confirmed after a member of the community reverse-engineered XLoader and found that it had the same executable as Formbook.

The data stealer is distributed in the form of malware-as-a-service and stands out from competing malware by being drop-dead simple to use, outfitting even code dummies with a multipurpose malware tool. According to the report, FormBook disappeared from malware markets in 2018, then rebranded to XLoader in 2020.

A malicious campaign that has set its sights on industrial-related entities in the Middle East since 2019 has resurfaced with an upgraded malware toolset to strike both Windows and macOS operating systems, symbolizing an expansion in both its targets and its strategy around distributing threats. WildPressure first came to light in March 2020 based off of a malware operation distributing a fully-featured C++ Trojan dubbed "Milum" that enabled the threat actor to gain remote control of the compromised device.