Security News

ESET researchers first spotted the new malware in April 2022 and named it CloudMensis because it uses pCloud, Yandex Disk, and Dropbox public cloud storage services for command-and-control communication. CloudMensis' capabilities clearly show that its operators' main goal is to collect sensitive info from infected Macs through various means.
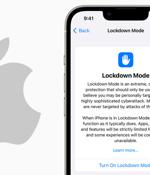
Apple on Wednesday announced it plans to introduce an enhanced security setting called Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura to safeguard high-risk users against "Highly targeted cyberattacks." Lockdown Mode, when enabled, "Hardens device defenses and strictly limits certain functionalities, sharply reducing the attack surface that potentially could be exploited by highly targeted mercenary spyware," Apple said in a statement.

A new hardware attack targeting Pointer Authentication in Apple M1 CPUs with speculative execution enables attackers to gain arbitrary code execution on Mac systems. Discovered by researchers at MIT's Computer Science & Artificial Intelligence Laboratory, this new class of attack would allow threat actors with physical access to Macs with Apple M1 CPUs to access the underlying filesystem.

Zoom has fixed a security flaw in its video-conferencing software that a miscreant could exploit with chat messages to potentially execute malicious code on a victim's device. The upshot is that someone who can send you chat messages could cause your vulnerable Zoom client app to install malicious code, such as malware and spyware, from an arbitrary server.

Another malicious Python package has been spotted in the PyPI registry performing supply chain attacks to drop Cobalt Strike beacons and backdoors on Windows, Linux, and macOS systems. PyPI is a repository of open-source packages that developers can use to share their work or benefit from the work of others, downloading the functional libraries required for their projects.

Apple has released security updates to address a zero-day vulnerability that threat actors can exploit in attacks targeting Macs and Apple Watch devices. In security advisories issued on Monday, Apple revealed that they're aware of reports this security bug "May have been actively exploited."

Apple on Thursday rolled out emergency patches to address two zero-day flaws in its mobile and desktop operating systems that it said may have been exploited in the wild. Both the vulnerabilities have been reported to Apple anonymously.

Apple has released security updates on Thursday to address two zero-day vulnerabilities exploited by attackers to hack iPhones, iPads, and Macs. In security advisories published today, Apple said that they're aware of reports the issues "May have been actively exploited."

The latest raft of non-emergency Apple security updates are out, patching a total of 87 different CVE-rated software bugs across all Apple products and plaforms. With 87 noteworthy bugs in the mix, there are plenty of security issues to choose from, including several that are listed with a warning that the bug might "Lead to arbitrary code execution", or even that it might be exploitable "To execute arbitrary code with kernel privileges".

Here on Naked Security, we've been lamenting the mysterious nature of Apple's security updates for ages. In the sudo bug case, Apple did eventually come to the party, and updated its own products in September.