Security News

A seven-year-old privilege escalation vulnerability discovered in the polkit system service could be exploited by a malicious unprivileged local attacker to bypass authorization and escalate permissions to the root user. Tracked as CVE-2021-3560, the flaw affects polkit versions between 0.113 and 0.118 and was discovered by GitHub security researcher Kevin Backhouse, who said the issue was introduced in a code commit made on Nov. 9, 2013.

Kali Linux 2021.2 released: Kaboxer, Kali-Tweaks, new tools, and more!Offensive Security has released Kali Linux 2021.2, the latest version of its popular open source penetration testing platform. June 2021 Patch Tuesday forecast: Patch management is back in the spotlightEvery day you look in the security news, there are reports of new ransomware attacks.

CloudLinux announces the release of CloudLinux OS Solo. "Our starting point was clear. Based on research results, our clients overwhelmingly want the classic CloudLinux OS with VPS and VMs, which only a few users can then utilize. One main request is a robust set of CloudLinux features on one server at affordable prices. Consequently, we found hundreds of VPSs with five or fewer websites hosted by a single client, many of which use VMs for staging and production. Some clients want a stable OS with technical support that is secure and not open-sourced."

Kali Linux 2021.2 was released today by Offensive Security and includes new themes and features, such as access to privileged ports, new tools, and a console-based configuration utility. Kali Linux is a Linux distribution designed for cybersecurity professionals and ethical hackers to perform penetration testing and security audits.

Offensive Security has released Kali Linux 2021.2, the latest version of its popular open source penetration testing platform. Offensive Security has introduced two new tools for making Kali easier to use: Kaboxer and Kali-Tweaks.

Windows 10 preview builds can now run Linux apps directly on the Windows 10 desktop using the new Windows Subsystem for Linux GUI. In this article, we go hands on with the new WSLg feature to demonstrate the types of graphical Linux apps you can now run. WSLg can launch Linux GUI apps by utilizing the Wayland server to display the apps in Windows 10.
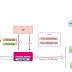
Cybersecurity researchers have disclosed a new backdoor program capable of stealing user login credentials, device information and executing arbitrary commands on Linux systems. The malware dropper has been dubbed "Facefish" by Qihoo 360 NETLAB team owing its capabilities to deliver different rootkits at different times and the use of Blowfish cipher to encrypt communications to the attacker-controlled server.

The team behind the popular pentesting Kali Linux distro has released Kaboxer, a tool to help penetration testers use older applications that don't work on modern operating systems, apps that need to run in isolation, and applications that are hard to package properly. "We hope to start to include more tools into Kali Linux that were previously not packable, and have you not realize that you are using them via Kaboxer," the team noted.

TuxCare services from CloudLinux provide automated security patches and updates for the systems supporting the Atlas V rocket. Through this work, TuxCare supports Department of Defense and Space Force missions to protect U.S. National Security.

Automated testing and rapid deployment are critical to defending against vulnerabilities in open source software, said David Wheeler, director of Open Source Supply Chain Security at the Linux Foundation. Wheeler referenced a 2021 report by software security and IoT company Synopsys which said there are an average of 528 open source components per application, that 84 per cent of codebases have at least one vulnerability, and the average number of vulnerabilities per codebase is 158.