Security News

The Monti ransomware gang has returned, after a two-month break from publishing victims on their data leak site, using a new Linux locker to target VMware ESXi servers, legal, and government organizations. Researchers at Trend Micro analyzing the new encryption tool from Monti found that it has "Significant deviations from its other Linux-based predecessors."
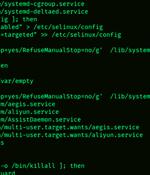
Vulnerable Redis services have been targeted by a "New, improved, dangerous" variant of a malware called SkidMap that's engineered to target a wide range of Linux distributions. "The malicious nature of this malware is to adapt to the system on which it is executed," Trustwave security researcher Radoslaw Zdonczyk said in an analysis published last week.
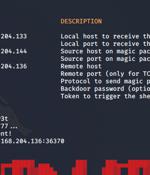
Threat actors are using an open-source rootkit called Reptile to target Linux systems in South Korea. "Unlike other rootkit malware that typically only provide concealment capabilities, Reptile goes a step further by offering a reverse shell, allowing threat actors to easily take control of systems," the AhnLab Security Emergency Response Center said in a report published this week.

The Abyss Locker operation is the latest to develop a Linux encryptor to target VMware's ESXi virtual machines platform in attacks on the enterprise. With VMware ESXi being one of the most popular virtual machine platforms, almost every ransomware gang has begun to release Linux encryptors to encrypt all virtual servers on a device.

Cybersecurity researchers have disclosed two high-severity security flaws in the Ubuntu kernel that could pave the way for local privilege escalation attacks. Cloud security firm Wiz, in a report shared with The Hacker News, said the easy-to-exploit shortcomings have the potential to impact 40% of Ubuntu users.

Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions."This vulnerability allows a remote attacker to potentially execute arbitrary commands on vulnerable OpenSSH's forwarded ssh-agent," Saeed Abbasi, manager of vulnerability research at Qualys, said in an analysis last week.

Earlier this month, security researchers discovered a new peer-to-peer malware with self-spreading capabilities that targets Redis instances running on Internet-exposed Windows and Linux systems. The Unit 42 researchers who spotted the Rust-based worm on July 11 also found that it hacks into Redis servers that have been left vulnerable to the maximum severity CVE-2022-0543 Lua sandbox escape vulnerability.
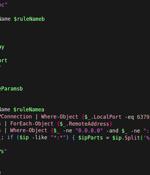
Cybersecurity researchers have uncovered a new cloud targeting, peer-to-peer worm called P2PInfect that targets vulnerable Redis instances for follow-on exploitation. "P2PInfect exploits Redis servers running on both Linux and Windows Operating Systems making it more scalable and potent than other worms," Palo Alto Networks Unit 42 researchers William Gamazo and Nathaniel Quist said.

Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service. According to Lumen's Black Lotus Labs threat research team, while the AVrecon remote access trojan compromised over 70,000 devices, only 40,000 were added to the botnet after gaining persistence.

Since at least May 2021, stealthy Linux malware called AVrecon was used to infect over 70,000 Linux-based small office/home office routers to a botnet designed to steal bandwidth and provide a hidden residential proxy service. According to Lumen's Black Lotus Labs threat research team, while the AVrecon remote access trojan compromised over 70,000 devices, only 40,00 were added to the botnet after gaining persistence.