Security News

Malicious local attackers can obtain full root access on Linux machines by taking advantage of a newly disclosed security flaw in the GNU C library (aka glibc). Tracked as CVE-2023-6246, the...

Unprivileged attackers can get root access on multiple major Linux distributions in default configurations by exploiting a newly disclosed local privilege escalation vulnerability in the GNU C Library. The bug is due to a heap-based buffer overflow weakness accidentally introduced in glibc 2.37 in August 2022 and later backported to glibc 2.36 when addressing a less severe vulnerability tracked as CVE-2022-39046.

Tsurugi Linux is a heavily customized open-source distribution focused on supporting DFIR investigations. The project focuses mainly on live forensics analysis, post-mortem analysis, and digital evidence acquisition.

AuthLogParser is an open-source tool tailored for digital forensics and incident response, specifically crafted to analyze Linux authentication logs. Log file, extracting crucial details like SSH logins, user creations, event names, IP addresses, among others.
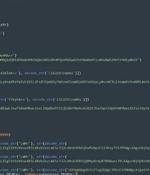
Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source repository with capabilities to deploy a cryptocurrency miner on affected Linux devices. The three...
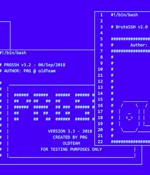
Poorly secured Linux SSH servers are being targeted by bad actors to install port scanners and dictionary attack tools with the goal of targeting other vulnerable servers and co-opting them into a...
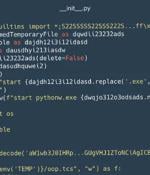
Cybersecurity researchers have identified a set of 116 malicious packages on the Python Package Index (PyPI) repository that are designed to infect Windows and Linux systems with a custom...

LogoFAIL is a constellation of two dozen newly discovered vulnerabilities that have lurked for years, if not decades, in Unified Extensible Firmware Interfaces responsible for booting modern devices that run Windows or Linux. The participating companies comprise nearly the entirety of the x64 and ARM CPU ecosystem, starting with UEFI suppliers AMI, Insyde, and Phoenix; device manufacturers such as Lenovo, Dell, and HP; and the makers of the CPUs that go inside the devices, usually Intel, AMD or designers of ARM CPUs.

Kali Linux 2023.4 released: New tools, Kali for Raspberry Pi 5, and more!OffSec has released Kali Linux 2023.4, the latest version of its penetration testing and digital forensics platform. Microsoft will offer extended security updates for Windows 10Microsoft will not abandon Windows 10 users to an insecure fate once it reaches end of support on October 14, 2025: both enterprises and individual consumers will be able receive Extended Security Updates, but will have to pay for them.

Widespread Windows and Linux Vulnerabilities Could Let Attackers Sneak in Malicious Code Before Boot
Widespread Windows and Linux Vulnerabilities Could Let Attackers Sneak in Malicious Code Before Boot Lenovo, AMI and Insyde have released patches for LogoFAIL, an image library poisoning attack. Researchers at firmware supply chain security platform company Binarly discovered a set of security vulnerabilities that open almost all Windows and Linux computers up to attack.