Security News

Recently patched vulnerabilities in MatrixSSL and wolfSSL, two open-source TLS/SSL implementations / libraries for embedded environments, have emphasized the great potential of using fuzzing to uncover security holes in implementations of cryptographic protocols. Fuzzing cryptographic libraries to flag security flaws.
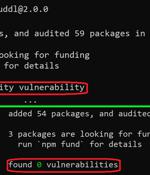
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.
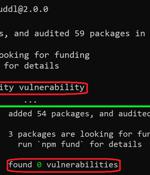
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.

Boffins at universities in France, Germany, Luxembourg, and Sweden took a deep dive into known Java deserialization vulnerabilities, and have now resurfaced with their findings. Log4Shell, the remote code execution flaw affecting the Apache Log4j logging library was made possible by Java deserialization.
In what's yet another instance of malicious packages creeping into public code repositories, 10 modules have been removed from the Python Package Index for their ability to harvest critical data points such as passwords and Api tokens. The packages "Install info-stealers that enable attackers to steal developer's private data and personal credentials," Israeli cybersecurity firm Check Point said in a Monday report.
Researchers have discovered a number of malicious Python packages in the official third-party software repository that are engineered to exfiltrate AWS credentials and environment variables to a publicly exposed endpoint. The list of packages includes loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, according to Sonatype security researcher Ax Sharma.

The hacker behind this hijack has now broken silence and explained his reasons to BleepingComputer. The hijacker of these libraries is an Istanbul-based security researcher, Yunus Aydın aka SockPuppets, who has attested to the fact when approached by BleepingComputer.

Yesterday, developers took notice of two hugely popular Python and PHP libraries, respectively, 'ctx' and 'PHPass' that had been hijacked, as first reported in the news by BleepingComputer. According to the hacker, rather "Security researcher," this was a bug bounty exercise and no malicious activity was intended.

The threat actor even replaced the older, safe versions of 'ctx' with code that exfiltrates the developer's environment variables, to collect secrets like Amazon AWS keys and credentials. Versions of a 'phpass' fork published to the PHP/Composer package repository Packagist had been altered to steal secrets in a similar fashion.

PyPI module 'ctx' that gets downloaded over 20,000 times a week has been compromised in a software supply chain attack with malicious versions stealing the developer's environment variables. The threat actor even replaced the older, safe versions of 'ctx' with code that exfiltrates the developer's environment variables, to collect secrets like Amazon AWS keys and credentials.