Security News

The U.S. Department of Justice unsealed an indictment charging three Iranian hackers with a "hack-and-leak" campaign that aimed to influence the 2024 U.S. presidential election. [...]

How to protect personal data Partner Content For people who haven't personally experienced them, terms like data leak or data breach may seem unfamiliar and foreign - much like visiting a new...

Dell has confirmed to BleepingComputer that they are investigating recent claims that it suffered a data breach after a threat actor leaked the data for over 10,000 employees. [...]

Better check your widgets, people Security researchers say that thousands of companies are potentially leaking secrets from their internal knowledge base (KB) articles via ServiceNow misconfigurations.…

Kawasaki Motors Europe has announced that it's recovering from a cyberattack that caused service disruptions as the RansomHub ransomware gang threatens to leak stolen data. [...]

A novel acoustic attack named 'PIXHELL' can leak secrets from air-gapped and audio-gapped systems, and without requiring speakers, through the LCD monitors they connect to. [...]

93GB of info feared pilfered in Montana by heartless crooks Planned Parenthood of Montana's chief exec says the org is responding to a cyber-attack on its systems, and has drafted in federal law...

French police reckon financial system targeted during Summer Games Nearly four weeks after the cyberattack on dozens of French national museums during the Olympic Games, the Brain Cipher...

Microsoft has released a new Windows 10 22H2 beta (KB5041582) with memory leak and crash fixes for Insiders in the Beta and Release Preview channels. [...]
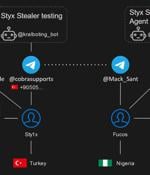
In what's a case of an operational security lapse, the operator behind a new information stealer called Styx Stealer leaked data from their own computer, including details related to the clients, profit information, nicknames, phone numbers, and email addresses. Styx Stealer, a derivative of the Phemedrone Stealer, is capable of stealing browser data, instant messenger sessions from Telegram and Discord, and cryptocurrency wallet information, cybersecurity company Check Point said in an analysis.