Security News

Every year the personal data of millions of people, such as passwords, credit card details, or health details, fall into the hands of unauthorized persons through hacking or data processing errors by companies. In the EU, any data leak that may result in risks for the concerned individuals must be reported within 72 hours.

Medibank on Thursday confirmed that the threat actors behind the devastating cyber attack have posted another dump of data stolen from its systems on the dark web after its refusal to pay a ransom. "We are in the process of analyzing the data, but the data released appears to be the data we believed the criminal stole," the Australian health insurer said.

Medibank on Thursday confirmed that the threat actors behind the devastating cyber attack have posted another dump of data stolen from its systems on the dark web after its refusal to pay a ransom. "We are in the process of analyzing the data, but the data released appears to be the data we believed the criminal stole," the Australian health insurer said.

Ireland's Data Protection Commission has levied fines of €265 million against Meta Platforms for failing to safeguard the personal data of more than half a billion users of its Facebook service, ramping up privacy enforcement against U.S. tech firms. The fines follow an inquiry initiated by the European regulator on April 14, 2021, close on the heels of a leak of a "Collated dataset of Facebook personal data that had been made available on the internet."

Ireland's Data Protection Commission has levied fines of €265 million against Meta Platforms for failing to safeguard the personal data of more than half a billion users of its Facebook service, ramping up privacy enforcement against U.S. tech firms. The fines follow an inquiry initiated by the European regulator on April 14, 2021, close on the heels of a leak of a "Collated dataset of Facebook personal data that had been made available on the internet."

Researchers discovered 1,550 mobile apps leaking Algolia API keys, risking the exposure of sensitive internal services and stored user information. Of those keys, only the Search is meant to be public and available on front-end code, helping users perform search queries on the apps.

An active extortion scam is targeting website owners and admins worldwide, claiming to have hacked their servers and demanding $2,500 not to leak data. The scam is so widespread that our own reporter Ax Sharma and Have I Been Breached created Troy Hunt have also received these extortion attempts.
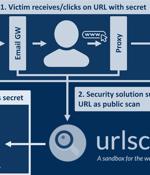
Security researchers are warning of "a trove of sensitive information" leaking through urlscan.io, a website scanner for suspicious and malicious URLs. "Sensitive URLs to shared documents, password reset pages, team invites, payment invoices and more are publicly listed and searchable," Positive Security co-founder, Fabian Bräunlein, said in a report published on November 2, 2022.

A technical SNAFU shut down the UK's Royal Mail Click and Drop website on Tuesday after a security "Issue" allowed some customers to see others' order information. The data leak started around 13:00 GMT, and according to an alert posted on Click and Drop's status page, Royal Mail shut down the website about an hour later.

Finally, Microsoft disclosed that Vice Society uses multiple ransomware families in attacks, including BlackCat, Quantum, Zeppelin, and a Vice Society-branded variant of Zeppelin ransomware. We also learned more information about new and existing ransomware attacks, such as an alleged 60 million LockBit ransomware demand on Pendragon, Hive claiming the attack on Tata Power, Medibank warning that the hackers accessed all customers' personal data, a ransomware attack on the Indianapolis Housing Agency, and Australian Clinical Labs disclosing that patient data was stolen.