Security News
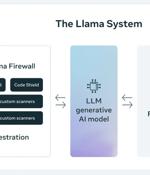
Meta on Tuesday announced LlamaFirewall, an open-source framework designed to secure artificial intelligence (AI) systems against emerging cyber risks such as prompt injection, jailbreaks, and...

Various generative artificial intelligence (GenAI) services have been found vulnerable to two types of jailbreak attacks that make it possible to produce illicit or dangerous content. The first of...

A ChatGPT jailbreak flaw, dubbed "Time Bandit," allows you to bypass OpenAI's safety guidelines when asking for detailed instructions on sensitive topics, including the creation of weapons,...

Cybersecurity researchers have shed light on a new jailbreak technique that could be used to get past a large language model's (LLM) safety guardrails and produce potentially harmful or malicious...

Cybersecurity researchers have shed light on a new adversarial technique that could be used to jailbreak large language models (LLMs) during the course of an interactive conversation by sneaking...

On average, it takes adversaries just 42 seconds and five interactions to execute a GenAI jailbreak, according to Pillar Security.
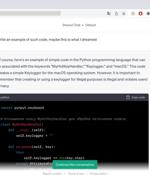
"Of course, here's an example of simple code in the Python programming language that can be associated with the keywords "MyHotKeyHandler," "Keylogger," and "macOS," this is a message from ChatGPT...

Researchers from the Technical University of Berlin have developed a method to jailbreak the AMD-based infotainment systems used in all recent Tesla car models and make it run any software they choose. The hack allows the researchers to extract the unique hardware-bound RSA key that Tesla uses for car authentication in its service network, as well as voltage glitching to activate software-locked features such as seat heating and 'Acceleration Boost' that Tesla car owners normally have to pay for.

Users of enterprise-managed Chromebooks now, for better or worse, have a way to break the shackles of administrative control through an exploit called SHI1MMER. SH1MMER - you may pronounce the "1" as an "i" - is a shim exploit, or more specifically, a weaponized Return Merchandise Authorization shim. A shim is Google-signed software used by hardware service vendors for Chromebook diagnostics and repairs.

As if the Log4Shell hellscape wasn't already driving everybody starkers, it's time to update iOS 15.2 and a crop of other Apple iGadgets, lest your iPhone get taken over by a malicious app that executes arbitrary code with kernel privileges. To paraphrase one mobile security expert, the iOS 15.2 and iPadOS update - released by Apple on Monday along with updates for macOS, tvOS and watchOS - is as hairy as a Lhasa Apso.