Security News

APT StormBamboo compromised a undisclosed internet service provider to poison DNS queries and thus deliver malware to target organizations, Volexity researchers have shared. In April 2023, ESET researchers documented the threat actor targeting an international NGO in China with malicious updates, but weren't able to pinpoint whether these updates were delivered through supply-chain compromise or adversary-in-the-middle attacks.
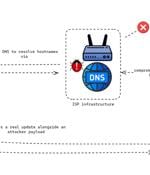
The China-linked threat actor known as Evasive Panda compromised an unnamed internet service provider to push malicious software updates to target companies in mid-2023, highlighting a new level of sophistication associated with the group. It was also found to have targeted an international non-governmental organization in Mainland China with MgBot delivered via update channels of legitimate applications like Tencent QQ. While it was speculated that the trojanized updates were either the result of a supply chain compromise of Tencent QQ's update servers or a case of an adversary-in-the-middle attack, Volexity's analysis confirms it's the latter stemming from a DNS poisoning attack at the ISP level.


A pro-Ukraine hacktivist group named 'Blackjack' has claimed a cyberattack against Russian provider of internet services M9com as a direct response to the attack against Kyivstar mobile operator. Kyivstar is Ukraine's largest telecommunications service provider and its services were severely disrupted in mid-December by what was later revealed to be an attack from Russian hackers.

The Turkish state-backed cyber espionage group tracked as Sea Turtle has been carrying out multiple spying campaigns in the Netherlands, focusing on telcos, media, internet service providers, and Kurdish websites. Previously, Sea Turtle, also known as Teal Kurma and Cosmic Wolf, focused on the Middle Eastern region, as well as Sweden and the United States, using techniques like DNS hijacking and traffic redirection to perform man-in-the-middle attacks against government and non-government organizations, media, ISPs, and IT service providers.

A US court has recently unsealed a restraining order against a gang of alleged cybercrooks operating outside the country, based on a formal legal complaint from internet giant Google. Interestingly the court order also authorises Google to identify network providers whose services directly or indirectly make this criminality possible, and to "[request] that those persons and entities take reasonable best efforts" to stop the malware and the data theft in its tracks.

The group uses two Windows-based malware that have been described as "Extremely complex" but there are indications of Linux malware, too. Researchers at SentinelLabs discovered Metador in an telecommunications company in the Middle East that had already been breached by about ten other threat actors originating from China and Iran, among them Moshen Dragon and MuddyWater.
The cybersecurity firm codenamed the group Metador in reference to a string "I am meta" in one of their malware samples and because of Spanish-language responses from the command-and-control servers. The threat actor is said to have primarily focused on the development of cross-platform malware in its pursuit of espionage aims.

The iOS application does not trigger any alert since it is signed with a certificate from a company named 3-1 Mobile SRL, enrolled in the Apple Developer Enterprise Program. The Android malicious software requires the targeted user to allow the installation of applications from unknown sources.

A week after it emerged that sophisticated mobile spyware dubbed Hermit was used by the government of Kazakhstan within its borders, Google said it has notified Android users of infected devices. Necessary changes have been implemented in Google Play Protect - Android's built-in malware defense service - to protect all users, Benoit Sevens and Clement Lecigne of Google Threat Analysis Group said in a Thursday report.