Security News

The threat actor targets high-profile and high-security accounts for cyberespionage purposes. Their favorite method to approach and attack their targets consists of using web beacons in emails before eventually attempting to harvest the target's credentials.
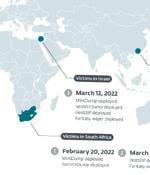
An Iranian advanced persistent threat actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong. The wiper, codenamed Fantasy by ESET, is believed to have been delivered via a supply chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.

Hackers with ties to the Iranian government have been linked to an ongoing social engineering and credential phishing campaign directed against human rights activists, journalists, researchers, academics, diplomats, and politicians working in the Middle East. The digital break-in entailed gaining access to their emails, cloud storage, calendars, and contacts, as well as exfiltrating the entire data associated with their Google accounts in the form of archive files through Google Takeout.

Iranian government-sponsored threat actors have been blamed for compromising a U.S. federal agency by taking advantage of the Log4Shell vulnerability in an unpatched VMware Horizon server. "Cyber threat actors exploited the Log4Shell vulnerability in an unpatched VMware Horizon server, installed XMRig crypto mining software, moved laterally to the domain controller, compromised credentials, and then implanted Ngrok reverse proxies on several hosts to maintain persistence," CISA noted.

Iranian state-sponsored cyber criminals used an unpatched Log4j flaw to break into a US government network, illegally mine for cryptocurrency, steal credentials and change passwords, and then snoop around undetected for several months, according to CISA. In an alert posted Wednesday, the US cybersecurity agency said it detected the advanced persistent threat activity on an unnamed federal civilian executive branch organization's network in April. "CISA and the Federal Bureau of Investigation assess that the FCEB network was compromised by Iranian government-sponsored APT actors," according to the alert.

The attackers compromised the federal network after hacking into an unpatched VMware Horizon server using an exploit targeting the Log4Shell remote code execution vulnerability. After deploying the cryptocurrency miner, the Iranian threat actors also set up reverse proxies on compromised servers to maintain persistence within the FCEB agency's network.

The Iranian threat actor known as Domestic Kitten has been attributed to a new mobile campaign that masquerades as a translation app to distribute an updated variant of an Android malware known as FurBall. "Since June 2021, it has been distributed as a translation app via a copycat of an Iranian website that provides translated articles, journals, and books," ESET researcher Lukas Stefanko said in a report shared with The Hacker News.

Several hacktivist groups are using Telegram and other tools to aid anti-government protests in Iran to bypass regime censorship restrictions amid ongoing unrest in the country following the death of Mahsa Amini in custody. The company said it has also witnessed sharing of proxies and open VPN servers to get around censorship and reports on the internet status in the country, with one group helping the anti-government demonstrators access social media sites.

The Federal Bureau of Investigation and CISA said that one of the Iranian threat groups behind the destructive attack on the Albanian government's network in July lurked inside its systems for roughly 14 months. "A FBI investigation indicates Iranian state cyber actors acquired initial access to the victim's network approximately 14 months before launching the destructive cyber attack, which included a ransomware-style file encryptor and disk wiping malware," the two agencies revealed in a joint advisory published today.

It has been a fairly quiet week on the ransomware front, with the biggest news being US sanctions on Iranians linked to ransomware attacks. Cisco has confirmed that the data leaked yesterday by the Yanluowang ransomware gang was stolen from the company network during a cyberattack in May. Lorenz ransomware breaches corporate network via phone systems.