Security News

The U.S. Department of Justice (DoJ) on Friday unsealed an indictment against an Iranian national for his alleged involvement in a multi-year cyber-enabled campaign designed to compromise U.S....

The US Department of Justice has unsealed an indictment accusing an Iranian national of a years-long campaign that compromised hundreds of thousands of accounts and attempting to infiltrate US defense contractors and multiple government agencies. "Nasab participated in a cyber campaign using spear phishing and other hacking techniques to infect more than 200,000 victim devices, many of which contained sensitive or classified defense information," said Damian Williams, US Attorney for the Southern District of New York.

The U.S. Department of Justice has unveiled an indictment against Alireza Shafie Nasab, a 39-year-old Iranian national, for his role in a cyber-espionage campaign targeting U.S. government and defense entities. The U.S. DoJ announcement says Nasab's job with Mahak Rayan Afraz was merely a front for the hacker's malicious operations.
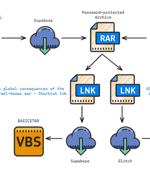
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar...

The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) announced sanctions against six officials associated with the Iranian intelligence agency for attacking critical...
High-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the U.K., and the U.S. have been targeted by an Iranian...

Microsoft says that a subgroup of the notorious APT35 Iranian-backed state hackers are targeting high-profile employees of research organizations and universities across Europe and the United States in spearphishing attacks pushing new MediaPL backdoor malware. MediaPL is a highly sophisticated malware strain designed to compromise the security of researchers and their data. The attackers have specifically targeted individuals involved in cutting-edge research, seeking unauthorized access to sensitive information. Microsoft's dedicated security teams have dissected the malware to better understand its functionality and devise effective countermeasures.

The recent wave of cyber attacks targeting Albanian organizations involved the use of a wiper called No-Justice. The findings come from cybersecurity company ClearSky, which said the Windows-based...

Iranian cyberspies are targeting defense industrial base organizations with a new backdoor called FalseFont, according to Microsoft. "We identified APT33 malware tied to an Iranian persona who may have been employed by the Iranian government to conduct cyber threat activity against its adversaries," the threat hunters said in an alert updated in October.

The Iranian nation-state actor known as MuddyWater has leveraged a newly discovered command-and-control (C2) framework called MuddyC2Go in its attacks on the telecommunications sector in Egypt,...