Security News

Indian budget airline SpiceJet on Wednesday attributed delayed flights to a ransomware attack. SpiceJet said the attack was quickly contained and rectified with flights again operating normally.

Low-cost Indian airline SpiceJet has informed its customers today of an attempted ransomware attack that has impacted some of its systems and caused delays on flight departures. ImportantUpdate: Certain SpiceJet systems faced an attempted ransomware attack last night that impacted and slowed down morning flight departures today.

Indian IT shops have been handed another extraordinarily short deadline within which to perform significant infosec work. MII boards must sign off on lists of critical systems.

India's computer and emergency response team, CERT-In, on Thursday published new guidelines that require service providers, intermediaries, data centers, and government entities to compulsorily report cybersecurity incidents, including data breaches, within six hours. "Any service provider, intermediary, data center, body corporate and Government organization shall mandatorily report cyber incidents to CERT-In within six hours of noticing such incidents or being brought to notice about such incidents," the government said in a release.

China-linked adversaries have been attributed to an ongoing onslaught against Indian power grid organizations, one year after a concerted campaign targeting critical infrastructure in the country came to light. Most of the intrusions involved a modular backdoor named ShadowPad, according to Recorded Future's Insikt Group, a sophisticated remote access trojan which has been dubbed a "Masterpiece of privately sold malware in Chinese espionage."

China has been accused of conducting a long-term cyber attack on India's power grid, and has been implicated in cyber attacks against targets in Ukraine. Cybersecurity firm Insikt Group found network intrusions at seven Indian State Load Dispatch Centers that conduct real-time operations for grid control and electricity dispatch, according to a report released Wednesday.

A threat actor of likely Pakistani origin has been attributed to yet another campaign designed to backdoor targets of interest with a Windows-based remote access trojan named CrimsonRAT since at least June 2021. "Their primary targets have been government and military personnel in Afghanistan and India. This campaign furthers this targeting and their central goal of establishing long term access for espionage."

A new campaign from the hacking group tracked as APT36, aka 'Transparent Tribe' or' Mythic Leopard,' has been discovered using new custom malware and entry vectors in attacks against the Indian government. The particular threat actor has been active since at least 2016, based in Pakistan, and its targets have historically been almost exclusively Indian defense and government entities.

A previously unknown hacking group has been linked to targeted attacks against human rights activists, human rights defenders, academics, and lawyers across India in an attempt to plant "Incriminating digital evidence." Cybersecurity firm SentinelOne attributed the intrusions to a group it tracks as "ModifiedElephant," an elusive threat actor that's been operational since at least 2012, whose activity aligns sharply with Indian state interests.
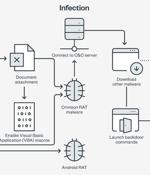
A politically motivated advanced persistent threat group has expanded its malware arsenal to include a new remote access trojan in its espionage attacks aimed at Indian military and diplomatic entities. Called CapraRAT by Trend Micro, the implant is an Android RAT that exhibits a high "Degree of crossover" with another Windows malware known as CrimsonRAT that's associated with Earth Karkaddan, a threat actor that's also tracked under the monikers APT36, Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe.