Security News
In the tumultuous landscape of cybersecurity, the year 2023 left an indelible mark with the brazen exploits of the Scattered Spider threat group. Their attacks targeted the nerve centers of major...

This policy from TechRepublic Premium provides information on defining an incident, assigning an incident response team, documenting a plan and conducting a response. DOCUMENT AN INCIDENT RESPONSE PLAN. Draw up a plan for incident response and start by including a detailed list of system/application/device information.

Athena AI, the new generative AI layer that spans across the entire Varonis Data Security Platform, redefines how security teams protect data - from visibility to action. Athena AI is embedded within the Varonis Data Security Platform and appears in a variety of user interfaces to speed up security and compliance tasks.

AWS Kill Switch is an open-source incident response tool for quickly locking down AWS accounts and IAM roles during a security incident. "I recently left my role as Sr. Director, Security Engineering at Robinhood and have been using my free time to sharpen my skills as an individual contributor and contribute to open source. I find it stimulating and a great way to build stronger ties with the security community," Jeffrey Lyon, the creator of AWS Kill Switch, told Help Net Security.
Modern security tools continue to improve in their ability to defend organizations’ networks and endpoints against cybercriminals. But the bad actors still occasionally find a way in. Security...

The policy's purpose is to define for employees, IT department staff and users the process to be followed when experiencing a suspected IT-security incident. Receiving strange unprompted messages, error windows or pop-up alerts.
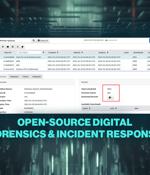
Velociraptor is a sophisticated digital forensics and incident response tool designed to improve your insight into endpoint activities. Velociraptor enables you to conduct precise and rapid collection of digital forensic data across multiple endpoints simultaneously.
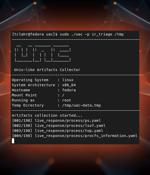
Unix-like Artifacts Collector (UAC) is a live response collection script for incident response that makes use of native binaries and tools to automate the collection of AIX, Android, ESXi,...

Automated incident response capabilities are not uniformly available across different security tools such as endpoint detection and response, and security information and event management as it largely depends on the vendor. Wazuh provides an active response module that performs automated incident response capabilities.

Abstract: Incident Response allows victim firms to detect, contain, and recover from security incidents. It should also help the wider community avoid similar attacks in the future.