Security News

Believed to be one of the leaders of the group, Arion Kurtaj, from Oxford, England, was arrested twice in 2022, first in January and then again in March, in connection with Lapsus$ hacking activity. Kurtaj used more than a dozen online names, White and Breachbase among them, and is believed to have made more than 300 BTC from his hacking activity, SIM-swapping included.

Security researchers have released NoFilter, a tool that abuses the Windows Filtering Platform to elevate a user's privileges to increases privileges to SYSTEM, the highest permission level on Windows. Microsoft defines the Windows Filtering Platform as "a set of API and system services that provide a platform for creating network filtering applications."

The U.S. Justice Department charged two Tornado Cash founders with helping criminals, including the notorious North Korean Lazarus hacking group, launder over $1 billion worth of stolen cryptocurrency through their decentralized crypto mixing service. Tornado Cash was also used to launder more than $96 million after the June Harmony Bridge hack and at least $7.8 million following the August Nomad Heist.

The FBI warned that North Koreans are likely readying to cash out tens of millions worth of stolen cryptocurrency out of hundreds of millions stolen in the last year alone. "The FBI believes the DPRK may attempt to cash out the bitcoin worth more than $40 million dollars."

Researchers from Italy and the UK have discovered four vulnerabilities in the TP-Link Tapo L530E smart bulb and TP-Link's Tapo app, which could allow attackers to steal their target's WiFi password. TP-link Tapo is a smart device management app with 10 million installations on Google Play.

A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially exploited by a threat actor to achieve remote code execution on Windows systems. Tracked as CVE-2023-40477, the vulnerability has been described as a case of improper validation while processing recovery volumes.

The China-aligned APT group known as 'Bronze Starlight' was seen targeting the Southeast Asian gambling industry with malware signed using a valid certificate used by the Ivacy VPN provider. According to SentinelLabs, which analyzed the campaign, the certificate belongs to PMG PTE LTD, a Singaporean vendor of the VPN product 'Ivacy VPN.'.

The flaw is tracked as CVE-2023-40477 and could give remote attackers arbitrary code execution on the target system after a specially crafted RAR file is opened.RARLAB released WinRAR version 6.23 on August 2nd, 2023, effectively addressing CVE-2023-40477.

Hackers claim to have breached the network of a major auction house and offered access to whoever was willing to pay $120,000. The most expensive item for sale was $120,000 for access to the network of a multi-billion dollar auction house.
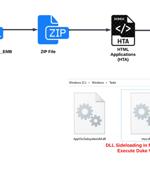
The phishing attacks feature PDF documents with diplomatic lures, some of which are disguised as coming from Germany, to deliver a variant of a malware called Duke, which has been attributed to APT29. "The threat actor used Zulip - an open-source chat application - for command-and-control, to evade and hide its activities behind legitimate web traffic," Dutch cybersecurity company EclecticIQ said in an analysis last week.