Security News

The free version of the popular WordPress plugin LiteSpeed Cache has fixed a dangerous privilege elevation flaw on its latest release that could allow unauthenticated site visitors to gain admin...

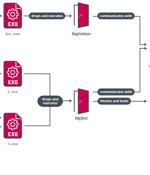
North Korean state-sponsored hackers – Jumpy Pisces, aka Andariel, aka Onyx Sleet – have been spotted burrowing into enterprise systems, then seemingly handing matters over to the Play ransomware...

The North Korean state-sponsored hacking group tracked as 'Andariel' has been linked to the Play ransomware operation, using the RaaS to work behind the scenes and evade sanctions. [...]

A global large-scale dubbed "EmeraldWhale" exploited misconfigured Git configuration files to steal over 15,000 cloud account credentials from thousands of private repositories. [...]

Midnight Blizzard – a cyber espionage group that has been linked to the Russian Foreign Intelligence Service (SVR) – is targeting government, academia, defense, and NGO workers with phishing...
A government entity and a religious organization in Taiwan were the target of a China-linked threat actor known as Evasive Panda that infected them with a previously undocumented post-compromise...

The FBI and the U.S. Cybersecurity & Infrastructure Security Agency (CISA) have disclosed that Chinese hackers breached commercial telecommunication service providers in the United States. [...]

The fourth day of Pwn2Own Ireland 2024 marked the end of the hacking competition with more than $1 million in prizes for over 70 unique zero-day vulnerabilities in fully patched devices. [...]

The infamous cryptojacking group known as TeamTNT appears to be readying for a new large-scale campaign targeting cloud-native environments for mining cryptocurrencies and renting out breached...

The North Korean Lazarus hacking group exploited a Google Chrome zero-day tracked as CVE-2024-4947 through a fake decentralized finance (DeFi) game targeting individuals in the cryptocurrency space. [...]