Security News

Security researchers have discovered that Minecraft is the most heavily abused game title by cybercriminals, who use it to lure unsuspecting players into installing malware. Based on stats collected by the security firm between July 2021 and July 2022, Minecraft-related files accounted for roughly 25% of malicious files spreading via game brand abuse, followed by FIFA, Roblox, Far Cry, and Call of Duty.

High-profile companies and local governments located primarily in Asia are the subjects of targeted attacks by a previously undocumented espionage group dubbed Worok that has been active since late 2020. "Worok's toolset includes a C++ loader CLRLoad, a PowerShell backdoor PowHeartBeat, and a C# loader PNGLoad that uses steganography to extract hidden malicious payloads from PNG files," ESET researcher Thibaut Passilly said in a new report published today.

Cybersecurity researchers have offered insight into a previously undocumented software control panel used by a financially motivated threat group known as TA505. The control panel, called TeslaGun, is said to be used by the adversary to manage the ServHelper implant, working as a command-and-control framework to commandeer the compromised machines.

A reverse-proxy Phishing-as-a-Service platform called EvilProxy has emerged, promising to steal authentication tokens to bypass multi-factor authentication on Apple, Google, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and even PyPI. The service enables low-skill threat actors who don't know how to set up reverse proxies to steal online accounts that are otherwise well-protected. The difference between these phishing frameworks and EvilProxy is that the latter is far simpler to deploy, offers detailed instructional videos and tutorials, a user-friendly graphical interface, and a rich selection of cloned phishing pages for popular internet services.

TikTok denies recent claims it was breached, and source code and user data were stolen, telling BleepingComputer that data posted to a hacking forum is "Completely unrelated" to the company. The user shared screenshots of an alleged database belonging to the companies, which they say was accessed on an Alibaba cloud instance containing data for both TikTok and WeChat users.

Cybercriminals using Prynt Stealer to collect data from victims are being swindled by the malware developer, who also receives a copy of the info over Telegram messaging service. Prynt Stealer can steal cryptocurrency wallet information, sensitive info stored in web browsers, VPN account data, cloud gaming account details.
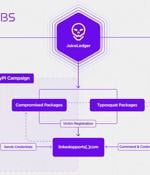
More details have emerged about the operators behind the first-known phishing campaign specifically aimed at the Python Package Index, the official third-party software repository for the programming language. The attacks received a significant facelift last month when the JuiceLedger actors targeted PyPi package contributors in a phishing campaign, resulting in the compromise of three packages with malware.

Researchers have identified functional similarities between a malicious component used in the Raspberry Robin infection chain and a Dridex malware loader, further strengthening the operators' connections to the Russia-based Evil Corp group. The findings suggest that "Evil Corp is likely using Raspberry Robin infrastructure to carry out its attacks," IBM Security X-Force researcher Kevin Henson said in a Thursday analysis.

The government of Montenegro has provided more information about the attack on its critical infrastructure saying that ransomware is responsible for the damage and disruptions. Public Administration Minister Maras Dukaj stated on local television yesterday that behind the attack is an organized cybercrime group.

Neopets has released details about the recently disclosed data breach incident that exposed personal information of more than 69 million members. Findings of the investigation launched on July 20, 2022 revealed that attackers had access to the Neopets IT systems from January 3, 2021 until July 19, 2022.