Security News
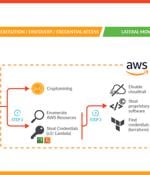
A sophisticated attack campaign dubbed SCARLETEEL is targeting containerized environments to perpetrate theft of proprietary data and software. "The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials," Sysdig said in a new report.

The APT27 hacking group, aka "Iron Tiger," has prepared a new Linux version of its SysUpdate custom remote access malware, allowing the Chinese cyberespionage group to target more services used in the enterprise. According to a new report by Trend Micro, the hackers first tested the Linux version in July 2022.

The U.S. Cybersecurity & Infrastructure Security Agency has added CVE-2022-36537 to its "Known Exploited Vulnerabilities Catalog" after threat actors began actively exploiting the remote code execution flaw in attacks. CVE-2022-36537 is a high-severity flaw impacting the ZK Framework versions 9.6.1, 9.6.0.1, 9.5.1.3, 9.0.1.2 and 8.6.4.1, enabling attackers to access sensitive information by sending a specially crafted POST request to the AuUploader component.

An advanced hacking operation dubbed 'SCARLETEEL' targets public-facing web apps running in containers to infiltrate cloud services and steal sensitive data. While the attackers deployed cryptominers in the compromised cloud environments, the hackers showed advanced expertise in AWS cloud mechanics, which they used to burrow further into the company's cloud infrastructure.

Some of the notable features include establishing a reverse shell with elevated privileges, uploading and downloading files, logging keystrokes, launching ransomware to encrypt files, and starting a live VNC session for real-time access. The cybersecurity firm assessed with moderate confidence that threat actors responsible for creating the malware are operating from North, East, or Southeast Asia and are likely former affiliates of the LockBit ransomware.

LastPass is, once again, telling customers about a security incident related to the August 2022 breach of its development environment and subsequent unauthorized access to the company's third-party cloud storage service that hosted backups: "The threat actor leveraged information stolen during the first incident, information available from a third-party data breach, and a vulnerability in a third-party media software package to launch a coordinated second attack." The second incident went initially unnoticed, LastPass says, the tactics, techniques, and procedures and the indicators of compromise of the second incident "Were not consistent with those of the first." It was only later determined that the two incidents were related.
The threat actor known as Blind Eagle has been linked to a new campaign targeting various key industries in Colombia. Blind Eagle, also known as APT-C-36, was recently covered by Check Point Research, detailing the adversary's advanced toolset comprising Meterpreter payloads that are delivered via spear-phishing emails.

A threat actor has posted data the alleged data stolen from American game publisher Activision in December 2022 on a hacking forum, highlighting the data's value for phishing operations. In a forum post to the Breached hacking forum, a website used by threat actors to sell and publish stolen data, the hackers claims to have stolen the data from Activision Azure database.

The Dutch police announced the arrest of three individuals in connection with a "Large-scale" criminal operation involving data theft, extortion, and money laundering. The Politie said its cybercrime team started the investigation nearly two years ago, in March 2021, after a large Dutch company suffered a security breach.

Dutch police have arrested three men for their alleged involvement with a ransomware gang that stole sensitive data and extorted hundreds of thousands of euros from thousands of companies. According to the Amsterdam police cybercrime team, the investigation began in March 2021 after a large Dutch company reported a case of data theft that had come accompanied by a ransom demand.