Security News

The U.S. Department of Justice (DoJ) has charged a 39-year-old U.K. national for perpetrating a hack-to-trade fraud scheme that netted him nearly $3.75 million in illegal profits. Robert Westbrook...

An X account hacking spree has fueled a successful pump-and-dump scheme for the $HACKED Solana token, with people rushing to buy the coin. [...]

The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) are alerting the public of false claims that the U.S. voter registration data has been...

42-year-old Nigerian national Bamidele Omotosho has been sentenced to 12 years and seven months in prison for his role in a series of cyber scams that resulted in millions of dollars in losses for...

Gambling blockchain Ronin Network suffered a security incident yesterday when white hat hackers exploited an undocumented vulnerability on the Ronin bridge to withdraw 4,000 ETH and 2 million...

Decentralized finance crypto exchange dYdX announced on Tuesday that the website for its older v3 trading platform has been compromised. dYdX also warned users not to visit or interact with the hacked dydx[.

The online forum OpenAI employees use for confidential internal communications was breached last year, anonymous sources have told The New York Times.Hackers lifted details about the design of the company's AI technologies from forum posts, but they did not infiltrate the systems where OpenAI actually houses and builds its AI. OpenAI executives announced the incident to the whole company during an all-hands meeting in April 2023, and also informed the board of directors.

E-commerce platform Shopify denies it suffered a data breach after a threat actor began selling customer data they claim was stolen from the company's network. [...]
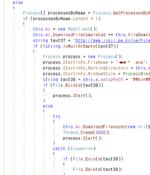
An unnamed South Korean enterprise resource planning (ERP) vendor's product update server has been found to be compromised to deliver a Go-based backdoor dubbed Xctdoor. The AhnLab Security...
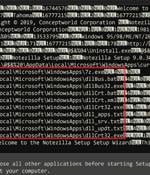
Installers for three different software products developed by an Indian company named Conceptworld have been trojanized to distribute information-stealing malware. The installers correspond to...