Security News

A new Android subscription malware named 'Fleckpe' has been spotted on Google Play, the official Android app store, disguised as legitimate apps downloaded over 620,000 times. Kaspersky reveals that Fleckpe is the newest addition to the realm of malware that generates unauthorized charges by subscribing users to premium services, joining the ranks of other malicious Android malware, such as Jocker and Harly.

A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads. An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea.

A new Android malware named 'Goldoson' has infiltrated Google Play through 60 legitimate apps that collectively have 100 million downloads. The malicious malware component is part of a third-party library used by all sixty apps that the developers unknowingly added to their apps.

The security researchers found that Google Play threats and Android phone infections are big business. A Google Play developer account can be bought for around $60-$200 USD depending on account characteristics such as the number of developed apps or the number of downloads.

Malware developers have created a thriving market promising to add malicious Android apps to Google Play for $2,000 to $20,000, depending on the type of malicious behavior cyber criminals request. The exact price for these services is negotiated on a case-by-case basis on hacker forums or Telegram channels, allowing cybercriminals to customize malicious Android apps with their own malware or functionality.

"The most popular application categories to hide malware and unwanted software include cryptocurrency trackers, financial apps, QR-code scanners, and even dating apps," Kaspersky said in a new report based on messages posted on online forums between 2019 and 2023. Dropper apps are the primary means for threat actors looking to sneak malware via the Google Play Store.

If you want to sneak malware onto people's Android devices via the official Google Play store, it may cost you about $20,000 to do so, Kaspersky suggests. Before cybercriminals can share their malicious apps from Google's official store, they'll need a Play developer account, and Kaspersky says those sell for between $60 and $200 each.

Google Play will be pushing Android app developers to allow users to delete their account and associated data from within the app. Google Play has introduced new app account deletion requirements and added Data deletion questions to developers' Data safety form.

On Android, Google offers its own authenticator app, unsurprisingly called Google Authenticator, that you can get from Google Play. Google's add-on app does the job of generating the needed one-time login code sequences, just like Apple's Settings > Passwords utility on iOS. But we're going to assume that at least some people, and possibly many, will perfectly reasonably have asked themselves, "What other authenticator apps are out there, so I don't have to put all my cybersecurity eggs into Apple's basket?".
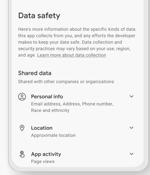
An investigation into data safety labels for Android apps available on the Google Play Store has uncovered "Serious loopholes" that allow apps to provide misleading or outright false information. The study, conducted by the Mozilla Foundation as part of its *Privacy Not Included initiative, compared the privacy policies and labels of the 20 most popular paid apps and the 20 most popular free apps on the app marketplace.