Security News
Google's Threat Analysis Group said on Wednesday that its researchers discovered commercial spyware called Heliconia that's designed to exploit vulnerabilities in Chrome and Firefox browsers as well as Microsoft Defender security software. The three components perform the following functions: Heliconia Noise is a web framework for deploying an exploit for a Chrome renderer bug followed by a sandbox escape; Heliconia Soft is a web framework that deploys a PDF containing a Windows Defender exploit; and Files is a set of Firefox exploits for Linux and Windows.
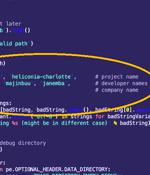
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.
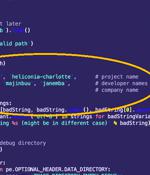
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.

Almost 300 apps, downloaded by around 15 million users, have been pulled from the Google Play and Apple App stores over claims they promised quick loans at reasonable rates but then used extortion and other predatory schemes against borrowers. Lookout contacted Google and Apple about the apps and said Wednesday that none of them were still available for download. "What's been identified is a tiny drop in the bucket overall," Chris Clements, vice president of solutions architecture for Cerberus Sentinel, told The Register, adding that "Anything over zero shouldn't be acceptable."

Google's Threat Analysis Group has linked an exploit framework that targets now-patched vulnerabilities in the Chrome and Firefox web browsers and the Microsoft Defender security app to a Spanish software company. While TAG is Google's team of security experts focused on protecting Google users from state-sponsored attacks, it also keeps track of dozens of companies that enable governments to spy on dissidents, journalists, and political opponents using surveillance tools.

Week in review: 5 free CISA resources, surviving a DDoS attack, Google to make Cobalt Strike useless
5G can reduce - but also create - security riskIn this interview with Help Net Security, Anubhav Arora, VP of Security Engineering at Cradlepoint, talks about the most common 5G security misconceptions, how to make sure the network is safe, but also how 5G can benefit businesses. 5 free resources from the Cybersecurity and Infrastructure Security AgencyThe Cybersecurity and Infrastructure Security Agency is an agency of the United States Department of Homeland Security.

Google has released an emergency security update for the desktop version of the Chrome web browser, addressing the eighth zero-day vulnerability exploited in attacks this year.As users need time to apply the security update on their Chrome installations, Google has withheld details about the vulnerability to prevent expanding its malicious exploitation.

An information-stealing Google Chrome browser extension named 'VenomSoftX' is being deployed by Windows malware to steal cryptocurrency and clipboard contents as users browse the web. This Chrome extension is being installed by the ViperSoftX Windows malware, which acts as a JavaScript-based RAT and cryptocurrency hijacker.

The Google Cloud Threat Intelligence team has open-sourced YARA Rules and a VirusTotal Collection of indicators of compromise to help defenders detect Cobalt Strike components in their networks. "We are releasing to the community a set of open-source YARA Rules and their integration as a VirusTotal Collection to help the community flag and identify Cobalt Strike's components and its respective versions," said Google Cloud Threat Intelligence security engineer Greg Sinclair.

Google Cloud's intelligence research and applications team has created and released a collection of 165 YARA rules to help defenders flag Cobalt Strike components deployed by attackers. Cobalt Strike, a legitimate adversary simulation tool used by pentesters and cyber red teams, has also become threat actors' preferred post-exploitation tool.