Security News

Over a dozen security flaws have been discovered in baseboard management controller firmware from Lanner that could expose operational technology and internet of things networks to remote attacks. BMC refers to a specialized service processor, a system-on-chip, that's found in server motherboards and is used for remote monitoring and management of a host system, including performing low-level system operations such as firmware flashing and power control.

Over a dozen security flaws have been discovered in baseboard management controller firmware from Lanner that could expose operational technology and internet of things networks to remote attacks. BMC refers to a specialized service processor, a system-on-chip, that's found in server motherboards and is used for remote monitoring and management of a host system, including performing low-level system operations such as firmware flashing and power control.
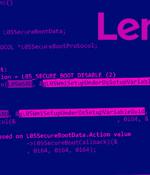
PC maker Lenovo has addressed yet another set of three shortcomings in the Unified Extensible Firmware Interface firmware affecting several Yoga, IdeaPad, and ThinkBook devices. "The vulnerabilities allow disabling UEFI Secure Boot or restoring factory default Secure Boot databases: all simply from an OS," Slovak cybersecurity firm ESET explained in a series of tweets.

A number of firmware security flaws uncovered in HP's business-oriented high-end notebooks continue to be left unpatched in some devices even months after public disclosure.Firmware flaws can have serious implications as they can be abused by an adversary to achieve long-term persistence on a device in a manner that can survive reboots and evade traditional operating system-level security protections.

In this Help Net Security video, Michael Thelander, Director Product Marketing at Eclypsium, discusses how financial organizations are failing to act despite the majority experiencing a firmware-related breach. 92% of CISOs in finance believe adversaries are better equipped at weaponizing firmware than their teams are at securing it, according to Eclypsium and Vanson Bourne.

A set of six high-severity firmware vulnerabilities impacting a broad range of HP Enterprise devices are still waiting to be patched, although some of them were publicly disclosed since July 2021. Firmware flaws are particularly dangerous because they can lead to malware infections that persist even between OS re-installations or allow long-term compromises that would not trigger standard security tools.

Firmware flaws are particularly dangerous because they can lead to malware infections that persist even between OS re-installations or allow long-term compromises that would not trigger standard security tools. As Binarly highlights in the report, even though it's been a month since they made some of the flaws public at Black Hat 2022, the vendor hasn't released security updates for all impacted models, leaving many customers exposed to attacks.

Networking equipment maker Zyxel has released patches for a critical security flaw impacting its network-attached storage devices. Tracked as CVE-2022-34747, the issue relates to a "Format string vulnerability" affecting NAS326, NAS540, and NAS542 models.

Networking device maker Zyxel is warning customers today of a new critical remote code execution vulnerability impacting three models of its Networked Attached Storage products. "A format string vulnerability was found in a specific binary of Zyxel NAS products that could allow an attacker to achieve unauthorized remote code execution via a crafted UDP packet," explains the advisory.
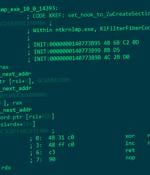
An unknown Chinese-speaking threat actor has been attributed to a new kind of sophisticated UEFI firmware rootkit called CosmicStrand. "The rootkit is located in the firmware images of Gigabyte or ASUS motherboards, and we noticed that all these images are related to designs using the H81 chipset," Kaspersky researchers said in a new report published today.