Security News

You can easily add a fingerprint reader to your computer if one isn't already built in.

A smartphone's unique Bluetooth fingerprint could be used to track the device's user-until now. A team of researchers has developed a simple firmware update that can completely hide the Bluetooth fingerprint, eliminating the vulnerability.

The Chameleon Android banking trojan has re-emerged with a new version that uses a tricky technique to take over devices - disable fingerprint and face unlock to steal device PINs. It does this by using an HTML page trick to acquire access to the Accessibility service and a method to disrupt biometric operations to steal PINs and unlock the device at will.

Security researchers Jesse D'Aguanno and Timo Teräs write that, with varying degrees of reverse-engineering and using some external hardware, they were able to fool the Goodix fingerprint sensor in a Dell Inspiron 15, the Synaptic sensor in a Lenovo ThinkPad T14, and the ELAN sensor in one of Microsoft's own Surface Pro Type Covers. These are just three laptop models from the wide universe of PCs, but one of these three companies usually does make the fingerprint sensor in every laptop we've reviewed in the last few years.

A new research has uncovered multiple vulnerabilities that could be exploited to bypass Windows Hello authentication on Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro X laptops....

Boffins at the University of California, Davis have devised a purportedly practical way to apply a memory abuse technique called Rowhammer to build unique, stable device fingerprints. UC Davis researchers Hari Venugopalan, Kaustav Goswami, Zainul Abi Din, Jason Lowe-Power, Samuel King, and Zubair Shafiq have found they can use Rowhammer to create device fingerprints in a brief amount of time that are unique and unchanging, even when the devices come from the same maker, with identical hardware and software configurations.

Unlike password authentication, which requires a direct match between what is inputted and what's stored in a database, fingerprint authentication determines a match using a reference threshold. As a result, a successful fingerprint brute-force attack requires only that an inputted image provides an acceptable approximation of an image in the fingerprint database.
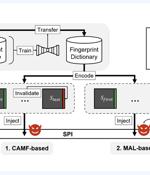
Researchers have discovered an inexpensive attack technique that could be leveraged to brute-force fingerprints on smartphones to bypass user authentication and seize control of the devices. The approach, dubbed BrutePrint, bypasses limits put in place to counter failed biometric authentication attempts by weaponizing two zero-day vulnerabilities in the smartphone fingerprint authentication framework.

The authors of the technical paper published on Arxiv.org also found that biometric data on the fingerprint sensors' Serial Peripheral Interface were inadequately protected, allowing for a man-in-the-middle attack to hijack fingerprint images. The idea of BrutePrint is to perform an unlimited number of fingerprint image submissions to the target device until the user-defined fingerprint is matched.

Chat Lock will create a new folder that can be locked with a password or biometric methods like a fingerprint. "Locking a chat takes that thread out of your inbox and puts it behind its own folder that can only be accessed with your device's password or biometric, like a fingerprint," WhatsApp said today.