Security News
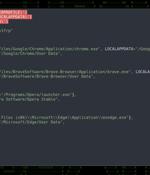
Cybersecurity researchers have unearthed a new Python-based attack campaign that leverages a Python-based remote access trojan to gain control over compromised systems since at least August 2022. LNK files retrieves two text files from a remote server that are subsequently renamed to.

The BlackCat ransomware isn't showing any signs of slowing down, and the latest example of its evolution is a new version of the gang's data exfiltration tool used for double-extortion attacks. BlackCat is considered a successor to Darkside and BlackMatter and is one of the most sophisticated and technically advanced Ransomware-as-a-service operations.

Crypto valuations have dropped, reducing the monetary appeal of ransomware attacks due to organizations mounting a formidable defense against ransomware. Instead, attackers on an information exfiltration mission will move vast amounts of proprietary data to systems that they control.

Browser synchronization abuse: Bookmarks as a covert data exfiltration channelTwo universal and seemingly innocuous browser features - the ability to create bookmarks and browser synchronization - make users' lives easier, but may also allow hackers to establish a covert data exfiltration channel. 6 ways your cloud data security policies are slowing innovation - and how to avoid thatAs practically every organization shifts from managing their data in network-based data centers to storing it in the cloud, cloud data security policies are created to secure this data in a cloud environment.
Two universal and seemingly innocuous browser features - the ability to create bookmarks and browser synchronization - make users' lives easier, but may also allow hackers to establish a covert data exfiltration channel. Some attackers have also recently managed to exploit Chrome's syncing feature and use an extension to connect their computer directly to a targeted workstation, creating a covert channel for remote data manipulation, but also for data exfiltration and C&C communication.

Two client-side risks dominate the problems with data loss and data exfiltration: improperly placed trackers on websites and web applications and malicious client-side code pulled from third-party repositories like NPM. Client-side security researchers are finding that improperly placed trackers, while not intentionally malicious, are a growing problem and have clear and significant privacy implications when it comes to both compliance/regulatory concerns, like HIPAA or PCI DSS 4.0. The government agency points out that sensitive health information combined with the shadowy data security practices used by technology companies is extremely problematic, with most customers having little or no knowledge of how their data is collected, what data is collected, how it is used, or how it is protected.

As a result, the Great Resignation has become the "Great Exfiltration," as people leaving their jobs may also be taking company data with them. Considering the Great Exfiltration, it is vital for organizations to create and implement a robust data loss prevention strategy during the offboarding process to prevent any destruction or loss of data.

Most notably, the research reveals data exfiltration remains a significant threat and despite large investments in security tools, organizations are not confident they can stop data exfiltration. "Existing tools are no longer a sufficient measure to prevent data exfiltration. Anti data exfiltration provides a new approach in the ongoing fight against cyberattacks."

Cybercrime actors part of the Magecart group have latched on to a new technique of obfuscating the malware code within comment blocks and encoding stolen credit card data into images and other files hosted on the server, once again demonstrating how the attackers are continuously improving their infection chains to escape detection. "One tactic that some Magecart actors employ is the dumping of swiped credit card details into image files on the server [to] avoid raising suspicion," Sucuri Security Analyst, Ben Martin, said in a write-up.

Many data leaks are the result of data exfiltration or the illegal transfer of data from a device containing sensitive information to unauthorized parties. Also known as data exportation, data extrusion or simply data theft, data exfiltration is one of the final stages of the cyber kill-chain and the most important objective of advanced persistent threats.