Security News

The Akira ransomware operation uses a Linux encryptor to encrypt VMware ESXi virtual machines in double-extortion attacks against companies worldwide. BleepingComputer's analysis of the Linux encryptor shows it has a project name of 'Esxi Build Esxi6,' indicating the threat actors designed it specifically to target VMware ESXi servers.

VMware patched today a VMware ESXi zero-day vulnerability exploited by a Chinese-sponsored hacking group to backdoor Windows and Linux virtual machines and steal data.The cyber espionage group-tracked as UNC3886 by cybersecurity firm Mandiant who discovered the attacks-abused the CVE-2023-20867 VMware Tools authentication bypass flaw to deploy VirtualPita and VirtualPie backdoors on guest VMs from compromised ESXi hosts where they escalated privileges to root.

A new ransomware-as-service operation called MichaelKors has become the latest file-encrypting malware to target Linux and VMware ESXi systems as of April 2023. "In fact, VMware goes as far as to claim it's not required. This, combined with the popularity of ESXi as a widespread and popular virtualization and management system, makes the hypervisor a highly attractive target for modern adversaries."

An increasing number of ransomware operations are adopting the leaked Babuk ransomware source code to create Linux encryptors targeting VMware ESXi servers. "There is a noticeable trend that actors increasingly use the Babuk builder to develop ESXi and Linux ransomware," said SentinelLabs threat researcher Alex Delamotte.
Multiple threat actors have capitalized on the leak of Babuk ransomware code in September 2021 to build as many as nine different ransomware families capable of targeting VMware ESXi systems. "These variants emerged through H2 2022 and H1 2023, which shows an increasing trend of Babuk source code adoption," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.

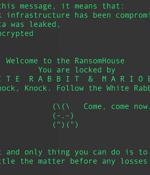
RTM Locker is the latest enterprise-targeting ransomware operation found to be deploying a Linux encryptor that targets virtual machines on VMware ESXi servers.At the time, Trellix and MalwareHunterTeam had only seen a Windows ransomware encryptor, but as Uptycs reported yesterday, RTM has expanded its targeting to Linux and VMware ESXi servers.
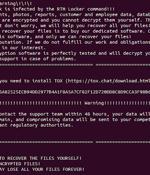
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system. "Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday.

VMware has released a vSphere ESXi update that addresses a known issue causing some Windows Server 2022 virtual machines to no longer boot after installing this month's KB5022842 update. Microsoft first acknowledged the issue on Thursday when the company said it only impacts VMs with Secure Boot enabled and running on vSphere ESXi 6.7 U2/U3 or vSphere ESXi 7.0.x. Although Redmond says that only VMware ESXi VMs are affected, some Windows admin reports hint at other hypervisor platforms being impacted by similar boot problems after deploying this month's updates.

Thousands of unpatched VMware ESXi servers hit by ransomware via old bugLate last week, unknown attackers launched a widespread ransomware attack hitting VMware ESXi hypervisors via CVE-2021-21974, an easily exploitable vulnerability that allows them to run exploit code remotely, without prior authentication. Reddit breached: Internal docs, dashboards, systems accessedPopular social news website and forum Reddit has been breached and the attacker "Gained access to some internal docs, code, as well as some internal dashboards and business systems," but apparently not to primary production systems and user data.

This subgroup, which is called Conti Team 1, released the Zion ransomware before rebranding it as Royal ransomware. Royal spread so fast because it became the ransomware making the biggest number of victims in November 2022, taking the lead in front of the LockBit ransomware.