Security News
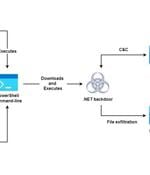
An active espionage campaign has been attributed to the threat actor known as Molerats that abuses legitimate cloud services like Google Drive and Dropbox to host malware payloads and for command-and-control and the exfiltration of data from targets across the Middle East. The cyber offensive is believed to have been underway since at least July 2021, according to cloud-based information security company Zscaler, continuing previous efforts by the hacking group to conduct reconnaissance on the target hosts and plunder sensitive information.

A large-scale cyber-espionage campaign targeting primarily renewable energy and industrial technology organizations have been discovered to be active since at least 2019, targeting over fifteen entities worldwide. The campaign was discovered by security researcher William Thomas, a Curated Intelligence trust group member, who employed OSINT techniques like DNS scans and public sandbox submissions.
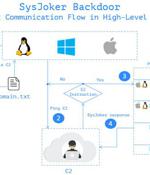
A new cross-platform backdoor called "SysJoker" has been observed targeting machines running Windows, Linux, and macOS operating systems as part of an ongoing espionage campaign that's believed to have been initiated during the second half of 2021. "SysJoker masquerades as a system update and generates its by decoding a string retrieved from a text file hosted on Google Drive," Intezer researchers Avigayil Mechtinger, Ryan Robinson, and Nicole Fishbein noted in a technical write-up publicizing their findings.
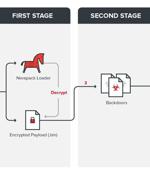
Transportation industry and government agencies related to the sector are the victims of an ongoing campaign since July 2020 by a sophisticated and well-equipped cyberespionage group in what appears to be yet another uptick in malicious activities that are "Just the tip of the iceberg." "The group tried to access some internal documents and personal information on the compromised hosts," Trend Micro researchers Nick Dai, Ted Lee, and Vickie Su said in a report published last week.

"Based on process lineage data, attackers seemed to use scripts extensively. These may be automated scripts used for collecting information and downloading additional tools," explains Symantec's report. Hidec: Command line tool for running a hidden window.

A corporate cyber-espionage hacker group has resurfaced after a seven-month hiatus with new intrusions targeting four companies this year, including one of the largest wholesale stores in Russia, while simultaneously making tactical improvements to its toolset in an attempt to thwart analysis. "In every attack, the threat actor demonstrates extensive red teaming skills and the ability to bypass traditional antivirus detection using their own custom malware," Group-IB's Ivan Pisarev said.

A crew of highly-skilled hackers specialized in corporate espionage has resumed activity, one of their victims this year being a large wholesale company in Russia. Active since 2018, RedCurl is responsible for at least 30 attacks against businesses in Russia, Ukraine, Canada, Norway, the UK, and Germany, the latest four of them occurring this year.

The study finds that the majority of rootkits are used by APT groups or financially motivated criminals whose payouts exceed the costs, the most commonly targeted are government and research institutes, and 77% of rootkits are used by cybercriminals for espionage purposes. Positive Technologies carried out a large-scale study of rootkits used by hacker groups over the past decade, starting in 2011.

Researchers have discovered a zero-day exploit for Microsoft Windows that was being used to elevate privileges and take over Windows servers as part of a Chinese-speaking advanced persistent threat espionage campaign this summer. As mentioned, the cybercriminals were using the exploit as part of a wider effort to install a remote shell on target servers, i.e., the MysterySnail malware, which was unknown prior to this campaign.

A Navy nuclear engineer and his wife were arrested under espionage-related charges alleging violations of the Atomic Energy Act after selling restricted nuclear-powered warship design data to a person they believed was a foreign power agent. Jonathan and Diana Toebbe sold the confidential information to an undercover FBI agent.