Security News

A China-based advanced persistent threat group is possibly deploying short-lived ransomware families as a decoy to cover up the true operational and tactical objectives behind its campaigns. The activity cluster, attributed to a hacking group dubbed Bronze Starlight by Secureworks, involves the deployment of post-intrusion ransomware such as LockFile, Atom Silo, Rook, Night Sky, Pandora, and LockBit 2.0.

A state-sponsored Chinese threat actor has used ransomware as a distraction to help it conduct electronic espionage, according to security software vendor Secureworks. Cybersecurity firm Secureworks asserts that ransomware is probably just a distraction from the true intent: cyber espionage.

Two Chinese hacking groups conducting cyber espionage and stealing intellectual property from Japanese and western companies are deploying ransomware as a decoy to cover up their malicious activities. Threat analysts from Secureworks say that the use of ransomware in espionage operations is done to obscure their tracks, make attribution harder, and create a powerful distraction for defenders.

Threat researcher Joey Chen of Sentinel Labs says he's spotted a decade worth of cyber attacks he's happy to attribute to a single Chinese gang. Chen has named the group Aoqin Dragon, says its goal is espionage, and that it prefers targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.

A previously undocumented Chinese-speaking advanced persistent threat actor dubbed Aoqin Dragon has been linked to a string of espionage-oriented attacks aimed at government, education, and telecom entities chiefly in Southeast Asia and Australia dating as far back as 2013. This involved leveraging old and unpatched security vulnerabilities, with the decoy documents enticing targets into opening the files.

A Chinese-speaking hacking group known as LuoYu is infecting victims WinDealer information stealer malware deployed by switching legitimate app updates with malicious payloads in man-on-the-side attacks. LuoYu has switched to abusing the automatic update mechanism of their victims' apps after previously pushing malware in easier to pull-off watering-hole attacks where they would use compromised local news sites as infection vectors.

Trend Micro says it patched a DLL hijacking flaw in Trend Micro Security used by a Chinese threat group to side-load malicious DLLs and deploy malware. As Sentinel Labs revealed in an early-May report, the attackers exploited the fact that security products run with high privileges on Windows to plant and load their own maliciously crafted DLL into memory, allowing them to elevate privileges and execute code.

Threat analysts have spotted a novel attack attributed to the Iranian hacking group known as APT34 group or Oilrig, who targeted a Jordanian diplomat with custom-crafted tools. The attack involved advanced anti-detection and anti-analysis techniques and had some characteristics that indicate lengthy and careful preparation.
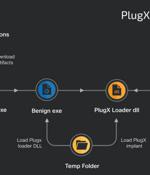
The China-based threat actor known as Mustang Panda has been observed refining and retooling its tactics and malware to strike entities located in Asia, the European Union, Russia, and the U.S. "Mustang Panda is a highly motivated APT group relying primarily on the use of topical lures and social engineering to trick victims into infecting themselves," Cisco Talos said in a new report detailing the group's evolving modus operandi. The group is known to have targeted a wide range of organizations since at least 2012, with the actor primarily relying on email-based social engineering to gain initial access to drop PlugX, a backdoor predominantly deployed for long-term access.

A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information. "The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as 'Viper,'" Cluster25 said in a report published last week.