Security News

Facebook's WhatsApp on Thursday began a global rollout of end-to-end encryption for message backups, which offers Android and iOS users with the ability to protect WhatsApp messages stored in Google Drive and Apple iCloud. WhatsApp claims no other similarly large global messaging service provides E2E encryption for users' stored communications and media - WhatsApp has more than 2bn users and in some regions serves as the de facto communications platform.

A new actor tracked as SnapMC has emerged in the cybercrime space, performing the typical data-stealing extortion that underpins ransomware operations, but without doing the file encryption part. File encryption is considered a core component of ransomware attacks, as it's the very element that brings operational disruption to the victim.

At the heart of all this, credential compromise is the leading cause of ransomware attacks, because credentials give hackers the access they need to hold your systems hostage. To understand the issue of credentials in ransomware attacks, one must understand what credentials really are.

End-to-end encryption isn't designed to secure messages against the intended recipients. New revelations about WhatsApp's moderator access to messages last week might seem like they run counter to the company's privacy-forward brand, but a closer look shows the messaging service's privacy protections remain in place and are operating as intended.

A recent study of enterprise IT security decision makers conducted by Tresorit shows that majority of enterprises use additional encryption methods to boost the security of cloud collaboration and file transfer tools with built-in end-to-end encryption are still less frequent despite the growing popularity of this privacy and security enhancing technology. Hybrid work era driving the need for external file sharing security.

The British government is preparing to launch a full-scale policy assault against Facebook as the company gears up to introduce end-to-end encryption across all of its services. The backlash has already begun, showing that officials face a tooth-and-nail fight to derail the rollout of end-to-end encryption on the anti-social networking site and others in the Facebook estate.

America's National Security Agency has published an FAQ about quantum cryptography, saying it does not know "When or even if" a quantum computer will ever exist to "Exploit" public-key cryptography. In the document, titled Quantum Computing and Post-Quantum Cryptography FAQ, the NSA said it "Has to produce requirements today for systems that will be used for many decades in the future." With that in mind, the agency came up with some predictions [PDF] for the near future of quantum computing and their impact on encryption.

The threat, dubbed LockFile, uses a unique "Intermittent encryption" method as a way to evade detection as well as adopting tactics from previous ransomware gangs. Discovered by researchers at Sophos, LockFile ransomware encrypts every 16 bytes of a file, which means some ransomware protection solutions don't notice it because "An encrypted document looks statistically very similar to the unencrypted original," Mark Loman, director, engineering, for next-gen technologies at Sophos, wrote in a report on LockFile published last week.
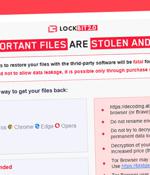
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "Intermittent encryption." Called LockFile, the operators of the ransomware have been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware that scrambles only every alternate 16 bytes of a file, thereby giving it the ability to evade ransomware defences.
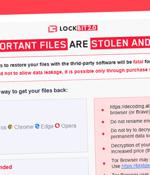
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "Intermittent encryption." Called LockFile, the operators of the ransomware have been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware that scrambles only every alternate 16 bytes of a file, thereby giving it the ability to evade ransomware defences.