Security News

Cybersecurity researchers are calling attention to a new sophisticated malware called CoffeeLoader that's designed to download and execute secondary payloads. The malware, according to Zscaler...

EDR bypass and killer attacks are surging, yet many organizations continue to overlook this threat while they have become over-reliant on this security tool – particularly when preventing...

The Akira ransomware gang was spotted using an unsecured webcam to launch encryption attacks on a victim's network, effectively circumventing Endpoint Detection and Response (EDR), which was...

The Akira ransomware gang was spotted using an unsecured webcam to launch encryption attacks on a victim's network, effectively circumventing Endpoint Detection and Response (EDR), which was...
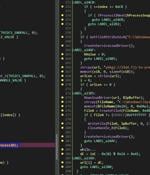
A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated with Adlice's product suite to sidestep detection efforts and deliver the Gh0st RAT malware. "To...
A newly devised technique leverages a Windows accessibility framework called UI Automation (UIA) to perform a wide range of malicious activities without tipping off endpoint detection and response...

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: 87,000+ Fortinet devices still open to attack, are yours among them? (CVE-2024-23113) Last week,...

Threat actors are leveraging the open-source EDRSilencer tool to evade endpoint detection and response systems, Trend Micro researchers have noticed. About EDRSilencer The software, which is...

The RansomHub ransomware gang has been using TDSSKiller, a legitimate tool from Kaspersky, to disable endpoint detection and response (EDR) services on target systems. [...]

Attackers are increasingly using new phishing toolkits (open-source, commercial, and criminal) to execute adversary-in-the-middle (AitM) attacks. AitM enables attackers to not just harvest...