Security News

Apple has released a firmware update for AirPods that could allow a malicious actor to gain access to the headphones in an unauthorized manner. Tracked as CVE-2024-27867, the authentication issue...

Researchers have discovered a new security vulnerability stemming from a design flaw in the IEEE 802.11 Wi-Fi standard that tricks victims into connecting to a less secure wireless network and...
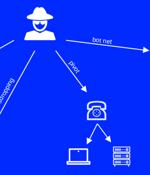
Multiple security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom's Zero Touch Provisioning that could be potentially exploited by a malicious attacker to conduct remote attacks. "An external attacker who leverages the vulnerabilities discovered in AudioCodes Ltd.'s desk phones and Zoom's Zero Touch Provisioning feature can gain full remote control of the devices," SySS security researcher Moritz Abrell said in an analysis published Friday.

Review and manage your consent Here's an overview of our use of cookies, similar technologies and how to manage them. Believing that it was safe to do so, she whispered the secret into a hole in the ground only to hear it broadcast far and wide.

The North Korean APT37 hacking group uses a new 'FadeStealer' information-stealing malware containing a 'wiretapping' feature, allowing the threat actor to snoop and record from victims' microphones. In a new report from the AhnLab Security Emergency Response Center, researchers provide information on new custom malware dubbed 'AblyGo backdoor' and 'FadeStealer' that the threat actors use in cyber espionage attacks.

Hiya has detected the newest scam call tactic, the eavesdropping scam. The new scam aims to get users to call back by leaving vague voicemail messages where an unknown voice is heard talking about the potential victim.

A security analyst has devised a way to capture Visual Voice Mail credentials on Android devices and then remotely listen to voicemail messages without the victim's knowledge. Visual Voice Mail is a voicemail system used by numerous mobile carriers that allow customers to view, listen to, and manage voicemails in any order.

Multiple security weaknesses have been disclosed in MediaTek system-on-chips that could have enabled a threat actor to elevate privileges and execute arbitrary code in the firmware of the audio processor, effectively allowing the attackers to carry out a "Massive eavesdrop campaign" without the users' knowledge. The discovery of the flaws is the result of reverse-engineering the Taiwanese company's audio digital signal processor unit by Israeli cybersecurity firm Check Point Research, ultimately finding that by stringing them together with other flaws present in a smartphone manufacturer's libraries, the issues uncovered in the chip could lead to local privilege escalation from an Android application.

MediaTek fixed security vulnerabilities that could have allowed attackers to eavesdrop on Android phone calls, execute commands, or elevate their privileges to a higher level. MediaTek is one of the largest semiconductor companies in the world, with their chips present in 43% of all smartphones as of the second quarter of 2021.

Check Point Research will today spill the beans on security holes it found within the audio processor firmware in millions of smartphones, which can be potentially exploited by malicious apps to secretly eavesdrop on people. Though its chips tend to power low-to-mid-end Android handhelds, MediaTek leads the world in terms of smartphone chip shipments; its tech is used nearly everywhere.