Security News
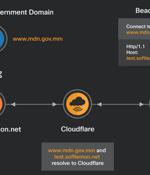
A malicious campaign has been found leveraging a technique called domain fronting to hide command-and-control traffic by leveraging a legitimate domain owned by the Myanmar government to route communications to an attacker-controlled server with the goal of evading detection. The threat, which was observed in September 2021, deployed Cobalt Strike payloads as a stepping stone for launching further attacks, with the adversary using a domain associated with the Myanmar Digital News network, a state-owned digital newspaper, as a front for their Beacons.

Secure messaging maker courts biz comms gigs with Psiphon's help Encrypted comms service Wickr has hooked up with Psiphon, a maker of censorship circumvention tools, to provide an alternative to...

Privacy services relying on the unsupported feature have been left high and dry

Secure messaging services and other privacy-oriented tools that rely on domain fronting to foil censorship efforts by various countries have been dealt a severe blow in the last month. First...

The messaging app Signal used a technique called domain fronting to misdirect censors in certain regions.

APT29, a/k/a Cozy Bear, has used Tor and a technique called domain fronting in order to secure backdoor access to targets for nearly two years running.
