Security News
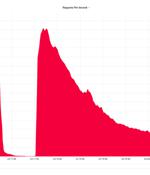
Web infrastructure company Cloudflare on Monday disclosed that it thwarted a record-breaking distributed denial-of-service attack that peaked at over 71 million requests per second. "The majority of attacks peaked in the ballpark of 50-70 million requests per second with the largest exceeding 71 million," the company said, calling it a "Hyper-volumetric" DDoS attack.

The number of DDoS attacks we see around the globe is on the rise, and that trend is likely to continue throughout 2023, according to Corero. We expect to see attackers deploy a higher rate of request-based or packets-per-second attacks.

This weekend, Cloudflare blocked what it describes as the largest volumetric distributed denial-of-service attack to date. "The majority of attacks peaked in the ballpark of 50-70 million requests per second with the largest exceeding 71 million rps," Cloudflare's Omer Yoachimik, Julien Desgats, and Alex Forster said.

Tor Project's Executive Director Isabela Dias Fernandes revealed on Tuesday that a wave of distributed denial-of-service attacks has been targeting the network since at least July 2022. "We have been working hard to mitigate the impacts and defend the network from these attacks. The methods and targets of these attacks have changed over time and we are adapting as these attacks continue."

A free tool aims is helping organizations defend against KillNet distributed-denial-of-service bots and comes as the US government issued a warning that the Russian cybercrime gang is stepping up its network flooding attacks against hospitals and health clinics. At current count, the KillNet open proxy IP blocklist lists tens of thousands of proxy IP addresses used by the Russian hacktivists in their network-traffic flooding events.

A new DDoS-as-a-Service platform named 'Passion' was seen used in recent attacks by pro-Russian hacktivists against medical institutions in the United States and Europe. "The Passion Botnet was leveraged during the attacks on January 27th, targeting medical institutions in the USA, Portugal, Spain, Germany, Poland, Finland, Norway, Netherlands, and the United Kingdom as retaliation for sending tanks in support of Ukraine," said Radware researchers.

In brief Russian hackers have proved yet again how quickly cyber attacks can be used to respond to global events with a series of DDoS attacks on German infrastructure and government websites in response to the country's plan to send tanks to Ukraine. Germany announced the transfer of 14 Leopard 2 A6 tanks to Ukraine on Wednesday, jointly with the US saying it would send 31 M1 Abrams tanks to the besieged nation.

DDoS attacks are getting larger and more complex moving towards mobile networks and IoT, which are now used in cyberwarfare. In this Help Net Security video, Steve Winterfeld, Advisory CISO at Akamai, discusses the most powerful DDoS attacks in the past 12 months.

A new Linux malware downloader created using SHC has been spotted in the wild, infecting systems with Monero cryptocurrency miners and DDoS IRC bots. According to ASEC researchers, who discovered the attack, the SHC loader was uploaded to VirusTotal by Korean users, with attacks generally focused on Linux systems in the same country.

According to NCC Group's Global Threat Intelligence team, November saw a 41% increase in ransomware attacks from 188 incidents to 265. In its most recent Monthly Threat Pulse, the group reported that the month was the most active for ransomware attacks since April this year.