Security News

With increased unidentified drone sightings worldwide, some are concerned they pose a cybersecurity risk. Learn more from Acronis about these risks and a real attack on a Taiwan drone manufacturer. [...]

The shared responsibility model: why securing AWS workloads is essential Partner Content Organizations are increasingly shifting their deployments to the cloud due to its many benefits over...

Get together with the European cybersecurity community at a two-day conference in London this December Sponsored Post This year's CyberThreat returns to London to provide a place for cybersecurity...
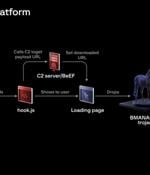
A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. "The threat actor behind this...

"Zero-day exploits are code vulnerabilities and loopholes that are unknown to software vendors, security researchers and the public. The term 'zero day' originates from the time remaining for a software vendor to patch buggy code. With zero days - or zero hours - to respond, developers are vulnerable to attack and have no time to patch the code and block the hole. One bug can give hackers enough access to explore and map internal networks, exfiltrate valuable data and find other attack vectors." Recent research found that, alongside financial implications, ransomware's impact could include heart attacks, strokes and PTSD. A ransomware attack is a form of data theft attack, and encrypting is not the only thing that attackers can do when they successfully obtain access to the data.

Sponsored Post Cyber security remains a top three priority for most, if not all, organisations. It's always a good idea for those new to the cyber security profession to learn about the tips and tools of the trade as early as possible.

93% of organizations find the execution of some essential security operation tasks, such as threat hunting, challenging, according to Sophos. IT professionals face challenging security operation tasks.

U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise and tactics, techniques, and procedures associated with the notorious LockBit 3.0 ransomware. "The LockBit 3.0 ransomware operations function as a Ransomware-as-a-Service model and is a continuation of previous versions of the ransomware, LockBit 2.0, and LockBit," the authorities said.
![S3 Ep114: Preventing cyberthreats – stop them before they stop you! [Audio + Text]](/static/build/img/news/s3-ep114-preventing-cyberthreats-stop-them-before-they-stop-you-audio-text-small.jpg)
DUCK. OK, so application control is Sophos's name for the ability to detect, and optionally to block, software that is not malware, but that a well-informed administrator might not want to support in their environment? DUCK. Now, my understanding is most so-called "Fileless malware" does involve files, probably quite a lot of files in its operation.

Australia has been the victim of damaging cyberattacks in the latter half of this year, with high-profile incidents impacting businesses across critical sectors such as telecoms, healthcare, and government. The Australian Cyber Security Centre recently confirmed what the media has already been reporting, releasing data that showed cyber-attacks have risen 13% YoY. What makes Australia such an attractive target? And what does this shift mean for the future of other countries around the world?