Security News

China appears to be entering a raging cyber-espionage battle that's grown in line with Russia's unprovoked attack on Ukraine, deploying advanced malware on the computer systems of Russian officials. China has tried to play a neutral role since Russia began its invasion of Ukraine on February 24, with government officials saying they want to see a peaceful resolution.

ESET Research discovered a still-ongoing cyberespionage campaign using a previously undocumented Korplug variant by the Mustang Panda APT group. The current campaign exploits the war in Ukraine and other European news topics.

The politically motivated Moses Staff hacker group has been observed using a custom multi-component toolset with the goal of carrying out espionage against its targets as part of a new campaign that exclusively singles out Israeli organizations. First publicly documented in late 2021, Moses Staff is believed to be sponsored by the Iranian government, with attacks reported against entities in Israel, Italy, India, Germany, Chile, Turkey, the U.A.E., and the U.S. Earlier this month, the hacker collective was observed incorporating a previously undocumented remote access trojan called "StrifeWater" that masquerades as the Windows Calculator app to evade detection.

Known Palestinian threat actor MoleRats is likely behind a recent malicious email campaign targeting Middle Eastern governments, foreign-policy think tanks and a state-affiliated airline with a new intelligence-gathering trojan dubbed NimbleMamba, researchers said. Researchers from Proofpoint said they have observed a spear-phishing campaign using multiple vectors since November that they believe is the work of TA402, more commonly known as MoleRats and linked to the Palestinian Territories, according to a report posted online Tuesday.

The Chinese hackers responsible for an attack on media giant News Corp last month likely were seeking intelligence to serve China's interests in a cyberespionage incident that shows the persistent vulnerability of corporate networks to email-based attacks, security professionals said. In an email to staff, News Corp cited a "Foreign government" as responsible for the "Persistent nation-state attack" and confirmed that "Some data" was stolen, according to published reports.
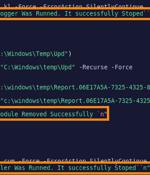
An advanced persistent threat group with links to Iran has updated its malware toolset to include a novel PowerShell-based implant called PowerLess Backdoor, according to new research published by Cybereason. The Boston-headquartered cybersecurity company attributed the malware to a hacking group known as Charming Kitten, while also calling out the backdoor's evasive PowerShell execution.

Cybersecurity researchers on Monday said they uncovered evidence of attempted attacks by a Russia-linked hacking operation targeting a Ukrainian entity in July 2021. Broadcom-owned Symantec, in a new report published Monday, attributed the attacks to an actor tracked as Gamaredon, a cyber-espionage collective known to be active since at least 2013.

A large-scale cyber-espionage campaign targeting primarily renewable energy and industrial technology organizations have been discovered to be active since at least 2019, targeting over fifteen entities worldwide. The campaign was discovered by security researcher William Thomas, a Curated Intelligence trust group member, who employed OSINT techniques like DNS scans and public sandbox submissions.

U.S. Cyber Command has confirmed that MuddyWater - an advanced persistent threat cyberespionage actor aka Mercury, Static Kitten, TEMP.Zagros or Seedworm that's historically targeted government victims in the Middle East - is an Iranian intelligence outfit. On Wednesday, USCYBERCOM not only confirmed the tie; it also disclosed the plethora of open-source tools and strategies MuddyWater uses to break into target systems and released malware samples.
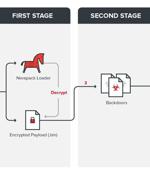
Transportation industry and government agencies related to the sector are the victims of an ongoing campaign since July 2020 by a sophisticated and well-equipped cyberespionage group in what appears to be yet another uptick in malicious activities that are "Just the tip of the iceberg." "The group tried to access some internal documents and personal information on the compromised hosts," Trend Micro researchers Nick Dai, Ted Lee, and Vickie Su said in a report published last week.