Security News

Two point-of-sale malware variants have been put to use by a threat actor to steal information related to more than 167,000 credit cards from payment terminals. While a significant proportion of attacks aimed at gathering payment data rely on JavaScript sniffers stealthily inserted on e-commerce websites, PoS malware continues to be an ongoing, if less popular, threat.

Harrington and Meiggs were charged in November 2019 for targeting at least ten victims in SIM swapping attacks and, in some cases, with death threats. According to the court documents, they allegedly stole $200,000 worth of cryptocurrency in one go from an Arizona resident who "Publicly communicated with cryptocurrency experts online," while $100,000 were swiped from a victim in California with close ties to someone who "Operated a blockchain-based business."

Fortifying cybersecurity defenses remains a work in progress for many organizations, who acknowledge their shortcomings but have yet to commit the necessary resources to the effort, according to...

Phishing attacks have only grown with the rise of SaaS in the workplace, and even the most security-savvy worker can be duped into a phishing attack. The turnkey platform allowed users to customise campaigns and create their own phishing tactics, providing them with over 100 phishing templates that copied known brand and services guidelines, kits, hosting and other tools.

The threat actor behind the malware-as-a-service called Eternity has been linked to new piece of malware called LilithBot. "The group has been continuously enhancing the malware, adding improvements such as anti-debug and anti-VM checks."

Fortifying cybersecurity defenses remains a work in progress for many organizations, who acknowledge their shortcomings but have yet to commit the necessary resources to the effort, according to new research from CompTIA. While a majority of respondents in each of seven geographic regions feels that their company's cybersecurity is satisfactory, CompTIA's "State of Cybersecurity" shows that a much smaller number rank the situation as "Completely satisfactory." Nearly everyone feels that there is room for improvement. "Companies are aware of the threats they face and the potential consequences of an attack or breach," said Seth Robinson, VP of industry research, CompTIA. "But they may be underestimating their exposure and how much they need to invest in cybersecurity. Risk mitigation is the key, the filter through which everything should be viewed."

Domain shadowing is a subcategory of DNS hijacking, where threat actors compromise the DNS of a legitimate domain to host their own subdomains for use in malicious activity but do not modify the legitimate DNS entries that already exist. These subdomains are then used to create malicious pages on the cybercriminals' servers while the domain owner's site's web pages and DNS records remain unchanged, and the owners don't realize they have been breached.

Critical Insight announced the release of the firm's H1 2022 Healthcare Data Breach Report, which analyzes breach data reported to the United States Department of Health and Human Services by healthcare organizations. This Help Net Security video reveals why attackers are changing targets and moving from large hospitals to smaller hospital systems.

With 3 billion players globally, the $200 billion gaming market is an increasingly ripe target for cybercriminals - with the perennially popular Minecraft one of the most targeted lures. Using statistics gathered by the Kaspersky Security Network, which processes anonymized threat data shared voluntarily by customers, the security vendor examined the most widespread malware strains that were found to have an association with the biggest games on PC and mobile.
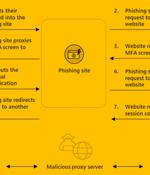
A new phishing-as-a-service toolkit dubbed EvilProxy is being advertised on the criminal underground as a means for threat actors to bypass two-factor authentication protections employed against online services. "EvilProxy actors are using reverse proxy and cookie injection methods to bypass 2FA authentication - proxifying victim's session," Resecurity researchers said in a Monday write-up.