Security News

Linux servers are the target of an ongoing campaign that delivers a stealthy malware dubbed perfctl with the primary aim of running a cryptocurrency miner and proxyjacking software. "Perfctl is...

Two suspects were arrested in Miami this week and charged with conspiracy to steal and launder over $230 million in cryptocurrency using crypto exchanges and mixing services. [...]

Cryptocurrency exchange Binance is warning of an "ongoing" global threat that's targeting cryptocurrency users with clipper malware with the goal of facilitating financial fraud. Clipper malware,...

Cybersecurity researchers are continuing to warn about North Korean threat actors' attempts to target prospective victims on LinkedIn to deliver malware called RustDoor. The latest advisory comes...

Cybersecurity researchers have uncovered a new malware campaign targeting Linux environments to conduct illicit cryptocurrency mining. The activity, which specifically singles out the Oracle...

The FBI says that 2023 was a record year for cryptocurrency fraud, with total losses exceeding $5.6 billion, based on nearly 70,000 reports received through the Internet Crime Complaint Center (IC3). [...]

Every type of fraud is on the rise, and 2023 was a particularly devastating year for victims of cryptocurrency and business email compromise (BEC) scams, according to the FBI. Cryptocurrency fraud...

"A cyber attack occurred in one of our wallets involving a loss of funds exceeding $230 million," the company said in a statement. The Mumbai-based company said the attack stemmed from a mismatch between the information that was displayed on Liminal's interface and what was actually signed.

A group of men behind a violent crime spree designed to compel victims to hand over access to their cryptocurrency savings. That announcement and the criminal complaint laying out charges against St. Felix focused largely on a single theft of cryptocurrency from an elderly North Carolina couple, whose home St. Felix and one of his accomplices broke into before physically assaulting the two victims-both in their seventies-and forcing them to transfer more than $150,000 in Bitcoin and Ether to the thieves' crypto wallets.
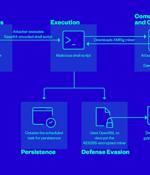
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.