Security News

Market, has had its web site seized by the United States Federal Bureau of Investigations. Market as "An invitation-only marketplace" from which buyers can acquire "Stolen credentials, cookies, and digital fingerprints that are gathered from compromised systems".

The domains for Genesis Market, one of the most popular marketplaces for stolen credentials of all types, were seized by law enforcement earlier this week as part of Operation Cookie Monster. While authorities have yet to publish press releases about the takedown, accessing the Genesis Market domains shows a banner saying that the FBI has executed a seizure warrant.

A new modular toolkit called 'AlienFox' allows threat actors to scan for misconfigured servers to steal authentication secrets and credentials for cloud-based email services. Researchers at SentinelLabs who analyzed AlienFox report that the toolset targets common misconfigurations in popular services like online hosting frameworks, such as Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.

Cross-platform exploit code is now available for a high-severity Backup Service vulnerability impacting Veeam's Backup & Replication software. The flaw affects all VBR versions and can be exploited by unauthenticated attackers to breach backup infrastructure after stealing cleartext credentials and gaining remote code execution as SYSTEM. Veeam released security updates to address this vulnerability for VBR V11 and V12 on March 7, advising customers using older releases to upgrade to secure vulnerable devices running unsupported releases.

Logged failed logins into a company's Okta domain could be used by threat actors to discover access credentials of valid accounts, Mitiga researchers have found. Those credentials can then be used log in to any of the organization's platforms that use Okta single sign-on or - if the login credentials belong to an administrator - to gain privileged access to other systems or restricted network areas.
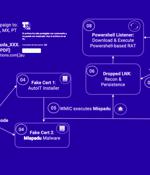
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads. "One of their main strategies is to compromise legitimate websites, searching for vulnerable versions of WordPress, to turn them into their command-and-control server to spread malware from there, filtering out countries they do not wish to infect, dropping different type of malware based on the country being infected," researchers Fernando García and Dan Regalado said.

Credential security company Beyond Identity has launched the Zero Trust Authentication initiative for organizations to hack-proof user credentials, with backing from major firms. In an effort to codify just how IT should apply that in practice, companies including Zero Scaler, Optiv, Palo Alto Networks, Crowdstrike and Ping Identity are supporting an initiative led by security firm Beyond Identify to lay out a zero trust architecture to inoculate corporate accounts and credentials against phishing and ransomware, among other threats.
A previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part of a cyber espionage campaign that has been active since at least June 2022. Prominent countries targeted include Azerbaijan, Tajikistan, Kyrgyzstan, Turkmenistan, and other Commonwealth of Independent States nations.

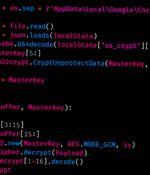
Morphisec, a security solution provider based in Israel, has reported that an advanced information stealer malware dubbed SYS01 is aimed at stealing access to Facebook business accounts and Chromium-based browsers' credentials. Morphisec's researcher has also seen the SYS01 malware attack critical government infrastructure employees, manufacturing companies and other industries.

Atlassian suffered a data leak after threat actors used stolen employee credentials to steal data from a third-party vendor. Atlassian confirmed to BleepingComputer that the compromised data was from third-party vendor Envoy which they use for in-office functions.