Security News

Oracle warned Apple customers to delay installing the latest macOS 14.4 Sonoma update because it will break Java on ARM-based Macs. According to Garcia-Ribeyro, since the Java Virtual Machine uses dynamic code generation and accesses memory in protected memory regions to ensure correctness and performance, its process will be terminated after deploying the macOS 14.4 update.
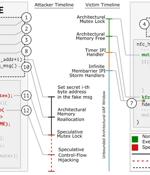
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the...

Vulnerable Docker services are being targeted by a novel campaign in which the threat actors are deploying XMRig cryptocurrency miner as well as the 9Hits Viewer software as part of a...

Researchers from the Vrije Universiteit Amsterdam have disclosed a new side-channel attack called SLAM that could be exploited to leak sensitive information from kernel memory on current and...

Academic researchers developed a new side-channel attack called SLAM that exploits hardware features designed to improve security in upcoming CPUs from Intel, AMD, and Arm to obtain the root password hash from the kernel memory. Short for Spectre based on LAM, the SLAM attack was discovered by researchers at Systems and Network Security Group at Vrije Universiteit Amsterdam, who demonstrated its validity by emulating the upcoming LAM feature from Intel on a last-generation Ubuntu system.

Citrix has released hotfixes for two vulnerabilities impacting Citrix Hypervisor, one of them being the "Reptar" high-severity flaw that affects Intel CPUs for desktop and server systems. "Although this is not an issue in the Citrix Hypervisor product itself, we have included updated Intel microcode to mitigate this CPU hardware issue," reads the advisory.

Intel has released fixes to close out a high-severity flaw codenamed Reptar that impacts its desktop, mobile, and server CPUs. Tracked as CVE-2023-23583 (CVSS score: 8.8), the issue has the...

Intel has fixed a high-severity CPU vulnerability in its modern desktop, server, mobile, and embedded CPUs, including the latest Alder Lake, Raptor Lake, and Sapphire Rapids microarchitectures. "Under certain microarchitectural conditions, Intel has identified cases where execution of an instruction encoded with a redundant REX prefix may result in unpredictable system behavior resulting in a system crash/hang, or, in some limited scenarios, may allow escalation of privilege from CPL3 to CPL0," Intel said.

A new software-based fault injection attack, CacheWarp, can let threat actors hack into AMD SEV-protected virtual machines by targeting memory writes to escalate privileges and gain remote code execution. This new attack exploits flaws in AMD's Secure Encrypted Virtualization-Encrypted State and Secure Encrypted Virtualization-Secure Nested Paging tech designed to protect against malicious hypervisors and reduce the attack surface of VMs by encrypting VM data and blocking attempts to alter it in any way.

A threat actor has been abusing Google Ads to distribute a trojanized version of the CPU-Z tool to deliver the Redline info-stealing malware. [...]