Security News

Internet services giant Cloudflare says it mitigated a record number of DDoS attacks in 2024, recording a massive 358% year-over-year jump and a 198% quarter-over-quarter increase. [...]

Modern websites are under constant pressure from automated traffic: scraping, credential stuffing, inventory hoarding, and other malicious bot behaviors. While Cloudflare Bot Management is a...

OPKSSH (OpenPubkey SSH) makes it easy to authenticate to servers over SSH using OpenID Connect (OIDC), allowing developers to ditch manually configured SSH keys in favor of identity provider-based...

Cloudflare has announced that its R2 object storage and dependent services experienced an outage lasting 1 hour and 7 minutes, causing 100% write and 35% read failures globally. [...]

Cloudflare announced that it closed all HTTP connections and it is now accepting only secure, HTTPS connections for api.cloudflare.com. [...]

An attempt to block a phishing URL in Cloudflare's R2 object storage platform backfired yesterday, triggering a widespread outage that brought down multiple services for nearly an hour. [...]

A security researcher discovered a flaw in Cloudflare's content delivery network (CDN), which could expose a person's general location by simply sending them an image on platforms like Signal and...

The largest distributed denial-of-service (DDoS) attack to date peaked at 5.6 terabits per second and came from a Mirai-based botnet with 13,000 compromised devices. [...]
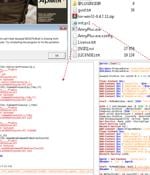
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed that a threat actor it tracks as UAC-0125 is leveraging Cloudflare Workers service to trick military personnel in the...
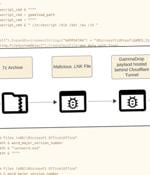
The threat actor known as Gamaredon has been observed leveraging Cloudflare Tunnels as a tactic to conceal its staging infrastructure hosting a malware called GammaDrop. The activity is part of an...