Security News
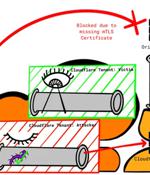
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of...

Cloudflare's Firewall and DDoS prevention can be bypassed through a specific attack process that leverages logic flaws in cross-tenant security controls. Specifically, the analyst identified two vulnerabilities in the system impacting Cloudflare's "Authenticated Origin Pulls" and "Allowlist Cloudflare IP Addresses."

Threat actors' use of Cloudflare R2 to host phishing pages has witnessed a 61-fold increase over the past six months. "The majority of the phishing campaigns target Microsoft login credentials, although there are some pages targeting Adobe, Dropbox, and other cloud apps," Netskope security researcher Jan Michael said.
New research has revealed that threat actors are abusing Cloudflare Tunnels to establish covert communication channels from compromised hosts and retain persistent access. "Cloudflared is functionally very similar to ngrok," Nic Finn, a senior threat intelligence analyst at GuidePoint Security, said.

Hackers are increasingly abusing the legitimate Cloudflare Tunnels feature to create stealthy HTTPS connections from compromised devices, bypass firewalls, and maintain long-term persistence. The technique isn't entirely new, as Phylum reported in January 2023 that threat actors created malicious PyPI packages that used Cloudflare Tunnels to stealthy steal data or remotely access devices.

Microsoft's Edge browser has recently enhanced its 'Edge Secure Network' feature, which now offers 5GB of data, significantly increasing from the previously offered 1GB. The Edge Secure Network uses Cloudflare's routing to encrypt your internet connection and secure your data against online threats, such as hacking attempts.Importantly, Microsoft ensures the user's Microsoft account identity is not shared with the service provider during a Secure Network connection.

Cloudflare announced on May 15, 2023 a new suite of zero-trust security tools for companies to leverage the benefits of AI technologies while mitigating risks.The Cloudflare One platform's new tools and features are Cloudflare Gateway, service tokens, Cloudflare Tunnel, Cloudflare Data Loss Prevention and Cloudflare's cloud access security broker.

Cloudflare has partnered with Kyndryl to help enterprises modernize and scale their corporate networks with managed WAN-as-a-Service and Cloudflare zero trust. "That's why with Kyndryl we've made it seamless for enterprises to be guided through the entire transition of bringing their corporate networks to the cloud," Prince added.

This weekend, Cloudflare blocked what it describes as the largest volumetric distributed denial-of-service attack to date. "The majority of attacks peaked in the ballpark of 50-70 million requests per second with the largest exceeding 71 million rps," Cloudflare's Omer Yoachimik, Julien Desgats, and Alex Forster said.

In yet another campaign targeting the Python Package Index repository, six malicious packages have been found deploying information stealers on developer systems. The malicious code, as is increasingly the case, is concealed in the setup script of these libraries, meaning running a "Pip install" command is enough to activate the malware deployment process.