Security News

Chrome browser extension 'SearchBlox' installed by more than 200,000 users has been discovered to contain a backdoor that can steal your Roblox credentials as well as your assets on Rolimons, a Roblox trading platform. These extensions claim to let you "Search Roblox servers for a desired player... blazingly fast" but both contained the backdoor.

An information-stealing Google Chrome browser extension named 'VenomSoftX' is being deployed by Windows malware to steal cryptocurrency and clipboard contents as users browse the web. This Chrome extension is being installed by the ViperSoftX Windows malware, which acts as a JavaScript-based RAT and cryptocurrency hijacker.
The Keksec threat actor has been linked to a previously undocumented malware strain, which has been observed in the wild masquerading as an extension for Chromium-based web browsers to enslave compromised machines into a botnet. Called Cloud9 by security firm Zimperium, the malicious browser add-on comes with a wide range of features that enables it to siphon cookies, log keystrokes, inject arbitrary JavaScript code, mine crypto, and even enlist the host to carry out DDoS attacks.

A new Chrome browser botnet named 'Cloud9' has been discovered in the wild using malicious extensions to steal online accounts, log keystrokes, inject ads and malicious JS code, and enlist the victim's browser in DDoS attacks. The Cloud9 browser botnet is effectively a remote access trojan for the Chromium web browser, including Google Chrome and Microsoft Edge, allowing the threat actor to remotely execute commands.

Google pushed out a bunch of security fixes for the Chrome and Chromium browser code earlier this week. In short, what we mean is that when Google says "It is aware of reports" of an attack launched by exploiting Chrome in real life, we're ready to assume that you can translate this into "The bug is real, and it really can be exploited, but because we didn't actually investigate the hacked system in real life ourselves, we're still on safe ground if we don't come straight out and say, 'Hey, everyone, it's an 0-day'."

Google has released an emergency security update for the Chrome desktop web browser to address a single vulnerability known to be exploited in attacks. The high-severity flaw is a type confusion bug in the Chrome V8 Javascript engine discovered and reported to Google by analysts at Avast.

Google on Thursday rolled out emergency fixes to contain an actively exploited zero-day flaw in its Chrome web browser. The vulnerability, tracked as CVE-2022-3723, has been described as a type confusion flaw in the V8 JavaScript engine.

Google announced today that the Google Chrome web browser will likely drop support for Windows 7 and 8.1 starting February 2023. After support is discontinued for these two Windows versions, the company says Chrome users must ensure that their devices are running at least Windows 10.

Researchers at Guardio Labs have discovered a new malvertizing campaign pushing Google Chrome extensions that hijack searches and insert affiliate links into webpages. Because all these extensions offer color customization options and arrive on the victim's machine with no malicious code to evade detection, the analysts named the campaign "Dormant Colors."
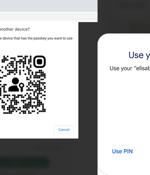
Google on Wednesday officially rolled out support for passkeys, the next-generation authentication standard, to both Android and Chrome. "Passkeys are a significantly safer replacement for passwords and other phishable authentication factors," the tech giant said.