Security News

Google has agreed to delete billions of data records collected from 136 million Chrome users in the United States, as part of a lawsuit settlement regarding alleged undisclosed browser data collection while in Incognito mode. Key elements of the Settlement include changes to Google's disclosures regarding its data collection practices, the deletion of billions of data records, implementing measures to curb the future accumulation of personal information, and eliminating mechanisms that enabled the tracking of users in Incognito mode without their knowledge.

Google fixed seven security vulnerabilities in the Chrome web browser on Tuesday, including two zero-days exploited during the Pwn2Own Vancouver 2024 hacking competition. Google fixed the two zero-days in the Google Chrome stable channel, version 123.0.6312.86/.87 for Windows and Mac and 123.0.6312.86 for Linux users, which will roll out worldwide over the coming days.

Microsoft is once again harassing Google Chrome users on Windows 10 and Windows 11 with popup desktop advertisements promoting Bing and its GPT-4 Bing Chat platform. The unsolicited ads are believed to be shown when users have Google Chrome open and configured to use Google as the default search engine.
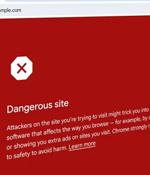
Google has introduced an updated Safe Browsing feature for Chrome on desktop and iOS, offering real-time protection against malicious sites while preserving user privacy. This enhancement allows Chrome to compare site URLs against Google's server-side database of known threats in real time, potentially blocking 25% more phishing attempts. Previously, Chrome relied on a locally-stored database updated every 30 to 60 minutes.The shift to server-side checks, announced in September 2023, aims to address the rapid growth of harmful websites and the brief existence of phishing domains. The new system checks URLs against cached safe URLs and previous Safe Browsing results. For URLs not in the cache,

Google will roll out a Safe Browsing update later this month that will provide real-time malware and phishing protection to all Chrome users, without compromising their browsing privacy. "Safe Browsing already protects more than 5 billion devices worldwide, defending against phishing, malware, unwanted software and more. In fact, Safe Browsing assesses more than 10 billion URLs and files every day, showing more than 3 million user warnings for potential threats," said Google's Jasika Bawa and Jonathan Li. "If we suspect a site poses a risk to you or your device, you'll see a warning with more information. By checking sites in real time, we expect to block 25% more phishing attempts. The new capability - also rolling out to Android later this month - uses encryption and other privacy-enhancing techniques to ensure that no one, including Google, knows what website you're visiting."

Millions of Chrome users now have a way to guard against the threat of extension subversion, that is, if they don't mind installing yet another browser extension. As we reported last August, those who develop Chrome extensions that become popular often receive solicitations to sell their code or to partner with a third-party in order for the new owner or partner to insert dubious, scammy, or malicious code in the extension.

Google is testing a new feature to prevent malicious public websites from pivoting through a user's browser to attack devices and services on internal, private networks. More simply, Google plans to prevent bad websites on the internet from attacking a visitor's devices in your home or on your computer.

Google has started testing the phasing out of third-party cookies on Chrome, affecting about 1% of its users or approximately 30 million people. Based on the test results and whether it causes significant issues with the displaying of websites, Google will begin to gradually phase out third-party cookies for the rest of its users starting in the third quarter of 2024.

Google fixes actively exploited Chrome zero-dayIn the new stable release of the Chrome browser, Google has fixed three security vulnerabilities affecting the V8 engine, including one zero-day with an existing exploit. With a constantly evolving threat landscape, cybersecurity awareness training is an essential component in creating a good security culture.

In the new stable release of the Chrome browser, Google has fixed three security vulnerabilities affecting the V8 engine, including one zero-day with an existing exploit.V8 is an open-source JavaScript and WebAssembly engine developed by the Chromium Project for Chromium and Google Chrome web browsers.