Security News

Critical flaw found inside the UNISOC smartphone chip. Check Point Research has identified what it is calling a critical security vulnerability in UNISOC's smartphone chip, which is responsible for cellular communication in 11% of the world's smartphones.

Trouble is brewing over moves by Taiwan to prevent China from gaining access to its chip technology, as the island nation proposes tougher laws to deter the leaking of trade secrets outside the country. China has reportedly hit back after Taiwanese Premier Su Tseng-chang called this week for a speedier introduction of legislation designed to protect the local semiconductor industry from what it sees as Chinese industrial espionage.

The Register broke the Meltdown story on January 2, 2018, as Intel and those who confidentially reported the security vulnerability were preparing to disclose them. To defend against Meltdown and Spectre, Intel and other affected vendors have had to add software and hardware mitigations that for some workloads make patched processors mildly to significantly slower.

Arm has made available for testing prototypes of its Morello architecture, aimed at bringing features into the design of CPUs that provide greater robustness and make them resistant to certain attack vectors. The Morello programme involves Arm collaborating with the University of Cambridge and others in tech to develop a processor architecture that is intended to be fundamentally more secure.

Lenovo at CES announced new ThinkPads with AMD's Ryzen chips, and the laptops will ship without Pluton turned on. "Pluton will be disabled by default on 2022 Lenovo ThinkPad platforms. Specifically the Z13, Z16, T14, T16, T14s, P16s and X13 using AMD 6000-series processors. Customers will have the ability to enable Pluton themselves," a Lenovo spokesperson told The Register.

"Pluton will be disabled by default on 2022 Lenovo ThinkPad platforms. Specifically the Z13, Z16, T14, T16, T14s, P16s and X13 using AMD 6000-series processors. Customers will have the ability to enable Pluton themselves," a Lenovo spokesperson told The Register. Pluton is designed for Windows PCs, and support for Linux "Is currently an unsupported scenario," Microsoft spokesperson told The Register.

Intel has removed support for SGX in 12th Generation Intel Core 11000 and 12000 processors, rendering modern PCs unable to playback Blu-ray disks in 4K resolution. This technical problem arises from the fact that Blu-ray disks require Digital Rights Management, which needs the presence of SGX to work.
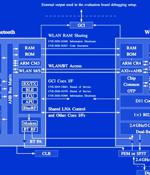
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "Combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless communications, such as Wi-Fi, Bluetooth, and LTE. "We provide empirical evidence that coexistence, i.e., the coordination of cross-technology wireless transmissions, is an unexplored attack surface," a group of researchers from the Technical University of Darmstadt's Secure Mobile Networking Lab and the University of Brescia said in a new paper.

Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it's possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device's Bluetooth component. To exploit these vulnerabilities, the researchers first needed to perform code execution on either the Bluetooth or WiFi chip.

Multiple security weaknesses have been disclosed in MediaTek system-on-chips that could have enabled a threat actor to elevate privileges and execute arbitrary code in the firmware of the audio processor, effectively allowing the attackers to carry out a "Massive eavesdrop campaign" without the users' knowledge. The discovery of the flaws is the result of reverse-engineering the Taiwanese company's audio digital signal processor unit by Israeli cybersecurity firm Check Point Research, ultimately finding that by stringing them together with other flaws present in a smartphone manufacturer's libraries, the issues uncovered in the chip could lead to local privilege escalation from an Android application.