Security News

China-linked adversaries have been attributed to an ongoing onslaught against Indian power grid organizations, one year after a concerted campaign targeting critical infrastructure in the country came to light. Most of the intrusions involved a modular backdoor named ShadowPad, according to Recorded Future's Insikt Group, a sophisticated remote access trojan which has been dubbed a "Masterpiece of privately sold malware in Chinese espionage."

Security researchers have uncovered a long-running malicious campaign from hackers associated with the Chinese government who are using VLC Media Player to launch a custom malware loader. Researchers at Symantec, a division of Broadcom, found that after gaining access to the target machine the attacker deployed a custom loader on compromised systems with the help of the popular VLC media player.
A Chinese state-backed advanced persistent threat group known for singling out Japanese entities has been attributed to a new long-running espionage campaign targeting new geographies, suggesting a "Widening" of the threat actor's targeting. "Victims in this Cicada campaign include government, legal, religious, and non-governmental organizations in multiple countries around the world, including in Europe, Asia, and North America," researchers from the Symantec Threat Hunter Team, part of Broadcom Software, said in a report shared with The Hacker News.
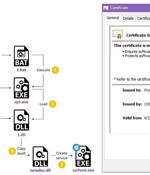
A Chinese advanced persistent threat tracked as Deep Panda has been observed exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy a backdoor and a novel rootkit on infected machines with the goal of stealing sensitive data. Cybersecurity firm CrowdStrike, which assigned the panda-themed name to the group all the way back in July 2014, called it "One of the most advanced Chinese nation-state cyber intrusion groups."

The Chinese hacking group Deep Panda is targeting VMware Horizon servers with the Log4Shell exploit to deploy a novel rootkit named 'Fire Chili. In a recent Deep Panda campaign discovered by Fortinet, the hacking group is deploying the new 'Fire Chili' rootkit to evade detection on compromised systems.

FCC adds Kaspersky, Chinese companies to list of potential threats to national security. The Federal Communications Commission's Public Safety and Homeland Security Bureau has added three companies to the list of communications equipment and services that pose a threat to national security through access to user information.

If ZTE and other Chinese giants defy bans on selling American technology to Russia, it will be because they can't help but chase the revenue, says Ashley Yablon, the whistleblower whose evidence led to ZTE being fined for willfully ignoring the US ban on exports to Iran. Yablon is a lawyer who, after working in senior roles at Huawei USA, in late 2011 became general counsel at Chinese telco kit-maker ZTE's US operations.

The U.S. Federal Communications Commission on Friday moved to add Russian cybersecurity company Kaspersky Lab to the "Covered List" of companies that pose an "Unacceptable risk to the national security" of the country. Also added alongside Kaspersky were China Telecom Corp and China Mobile International USA. The block list includes information security products, solutions, and services supplied, directly or indirectly, by the company or any of its predecessors, successors, parents, subsidiaries, or affiliates.

A Chinese-speaking threat actor called Scarab has been linked to a custom backdoor dubbed HeaderTip as part of a campaign targeting Ukraine since Russia embarked on an invasion last month, making it the second China-based hacking group after Mustang Panda to capitalize on the conflict. "The malicious activity represents one of the first public examples of a Chinese threat actor targeting Ukraine since the invasion began," SentinelOne researcher Tom Hegel said in a report published this week.

A China-based advanced persistent threat known as Mustang Panda has been linked to an ongoing cyberespionage campaign using a previously undocumented variant of the PlugX remote access trojan on infected machines. Slovak cybersecurity firm ESET dubbed the new version Hodur, owing to its resemblance to another PlugX variant called THOR that came to light in July 2021.