Security News

A threat actor with a suspected China nexus has been linked to a set of espionage attacks in the Philippines that primarily relies on USB devices as an initial infection vector. The reliance on infected USB drives to propagate the malware is unusual if not new.

The United States' Federal Communications Commission has barred itself from authorizing the import or sale of Chinese telecoms and video surveillance products from Huawei, ZTE, Hytera Communications, Hikvision, and Dahua, on national security grounds. As it is not legal to offer such products in the US without FCC approval, the move is effectively a ban on the five vendors' products.

The U.S. Federal Communications Commission formally announced it will no longer authorize electronic equipment from Huawei, ZTE, Hytera, Hikvision, and Dahua, deeming them an "Unacceptable" national security threat. All these Chinese telecom and video surveillance companies were previously included in the Covered List as of March 12, 2021.

The U.S. Federal Communications Commission formally announced it will no longer authorize electronic equipment from Huawei, ZTE, Hytera, Hikvision, and Dahua, deeming them an "Unacceptable" national security threat. All these Chinese telecom and video surveillance companies were previously included in the Covered List as of March 12, 2021.

The United Kingdom has decided Chinese video cameras have no place in government facilities. Government departments have also been "Advised that no such equipment should be connected to departmental core networks" and told to consider whether they should remove and replace Chinese video cameras "Deployed on sensitive sites" - and do so before planned upgrades.
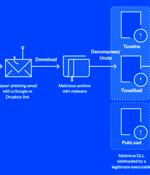
A notorious advanced persistent threat actor known as Mustang Panda has been linked to a spate of spear-phishing attacks targeting government, education, and research sectors across the world. Mustang Panda, also called Bronze President, Earth Preta, HoneyMyte, and Red Lich, is a China-based espionage actor believed to be active since at least July 2018.

State-backed Chinese hackers launched a spearphishing campaign to deliver custom malware stored in Google Drive to government, research, and academic organizations worldwide. The Chinese hackers used Google accounts to send their targets email messages with lures that tricked them into downloading custom malware from Google Drive links.
Users clicking on a link sent through the messaging app are directed to an actor-controlled site, which, in turn, sends them to a landing domain impersonating a well-known brand, from where the victims are once again taken to sites distributing fraudulent apps and bogus rewards. Attacks wherein scammy mobile ads are clicked from an Android device have been observed to culminate in the deployment of a mobile trojan called Triada, which was recently spotted propagating via fake WhatsApp apps.

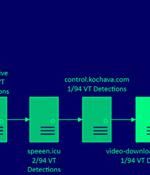
A cyberespionage threat actor tracked as Billbug has been running a campaign targeting a certificate authority, government agencies, and defense organizations in several countries in Asia. Symantec hasn't determined how Billbug gains initial access to the target networks but they have seen evidence of this happening by exploiting public-facing apps with known vulnerabilities.

A previously undocumented Android spyware tool named 'BadBazaar' has been discovered targeting ethnic and religious minorities in China, most notably the Uyghurs in Xinjiang. Uyghurs, a regional Muslim minority of roughly 13 million people, have suffered extreme oppression from the central Chinese government due to their cultural deviation from typical eastern Chinese values.