Security News

Google has revealed that it took down 1,320 YouTube channels and 1,177 Blogger blogs as part of a coordinated influence operation connected to the People’s Republic of China (PRC). "The...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Cybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that's believed to have been active since 2018. The intrusion singled out...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
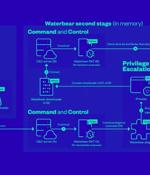
Interestingly, the RAT module is fetched twice from the attacker-controlled infrastructure, the first of which is just used to load the Waterbear plugin that subsequently launches a different version of the Waterbear downloader to retrieve the RAT module from another C&C server. Put differently, the first Waterbear RAT serves as a downloader while the second Waterbear RAT functions as a backdoor, harvesting sensitive information from the compromised host through a set of 60 commands.

The MITRE Corporation has offered more details into the recently disclosed cyber attack, stating that the first evidence of the intrusion now dates back to December 31, 2023. The attack,...

The recently uncovered cyber espionage campaign targeting perimeter network devices from several vendors, including Cisco, may have been the work of China-linked actors, according to new...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Discovered by Infoblox, the activity does not have a clear goal or motivation but demonstrates sophistication and advanced capabilities to manipulate global DNS systems. Muddling Meerkat manipulates DNS queries and responses by targeting the mechanism by which resolvers return the IP addresses.

A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated domain name system (DNS) activities in a likely effort to evade security measures and...