Security News

The Russian government has established its own TLS certificate authority to address issues with accessing websites that have arisen in the wake of sanctions imposed by the west following the country's unprovoked military invasion of Ukraine. According to a message posted on the Gosuslugi public services portal, the Ministry of Digital Development is expected to provide a domestic replacement to handle the issuance and renewal of TLS certificates should they get revoked or expired.

Russia has created its own trusted TLS certificate authority to solve website access problems that have been piling up after sanctions prevent certificate renewals. The sanctions imposed by western companies and governments are preventing Russian sites from renewing existing TLS certificates, causing browsers to block access to sites with expired certificates.

Threat actors are using stolen NVIDIA code signing certificates to sign malware to appear trustworthy and allow malicious drivers to be loaded in Windows. The leak includes two stolen code-signing certificates used by NVIDIA developers to sign their drivers and executables.

Threat actors are using stolen NVIDIA code signing certificates to sign malware to appear trustworthy and allow malicious drivers to be loaded in Windows. The leak includes two stolen code-signing certificates used by NVIDIA developers to sign their drivers and executables.

The particular provision requires web browsers like Chrome, Safari, and Firefox to accept QWACs, which practically compels browser developers and security advocates to ease their security stance. TLS certificates are vital for the online exchange of sensitive information with websites such as passwords, sensitive uploads, or payment details.

Let's Encrypt, a non-profit organization that helps people obtain free SSL/TLS certificates for websites, plans to revoke a non-trivial number of its certs on Friday because they were improperly issued. In a post to the Let's Encrypt discussion community forum, site reliability engineer Jillian Tessa explained that on Tuesday, a third party reported "Two irregularities" in the code implementing the "TLS Using ALPN" validation method in Boulder, its Automatic Certificate Management Environment software.

Let's Encrypt will begin revoking certain SSL/TLS certificates issued within the last 90 days starting January 28, 2022. As a non-profit certificate authority run by Internet Security Research Group, Let's Encrypt provides X.509 certificates for Transport Layer Security encryption at no cost.

Another CISO walks into a board meeting and muddles through stats showing their compliance status. In the classic risk management equation of Risk = Threat x Vulnerability, I have no control over the threat actor's motivation, skill, or resources.

The challenge faced by already strained IT teams is how to deliver strong certificate management across increasingly complex IT environments, at a time when workforces are massively distributed and entering the corporate network via the consumer-grade technologies in their homes. While third-party certificate authorities are a trusted option for many enterprises across the globe, many choose instead to issue them in-house, operating their own "Private CAs" to fulfill at least a portion of their PKI needs.
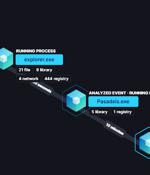
Cybersecurity researchers have disclosed details of an evasive malware campaign that makes use of valid code signing certificates to sneak past security defenses and stay under the radar with the goal of deploying Cobalt Strike and BitRAT payloads on compromised systems. The binary, a loader, has been dubbed "Blister" by researchers from Elastic Security, with the malware samples having negligible to zero detections on VirusTotal.