Security News

Browser extensions, also called add-ons, are mostly downloaded from official marketplaces or browser providers repositories, such as the Chrome Web Store or the Firefox Add-ons website. In 2020, 106 browser extensions were removed from the Chrome Web Store, being used to steal user data, take screen captures or even steal credit card information from web forms.

More than 1.31 million users attempted to install malicious or unwanted web browser extensions at least once, new findings from cybersecurity firm Kaspersky show. "From January 2020 to June 2022, more than 4.3 million unique users were attacked by adware hiding in browser extensions, which is approximately 70% of all users affected by malicious and unwanted add-ons," the company said.

Google has issued 11 security fixes for desktop Chrome, including one bug that has an exploit for it out in the wild. This is the fifth Chrome bug Google has fixed this year that has either been exploited or had exploit code in the wild.

The latest update to Google's Chrome browser is out, bumping the four-part version number to 104.0.5112.101, or to 104.0.5112.102. Chrome will probably update itself, but we always recommend checking anyway.

Almost 7 million users have attempted to install malicious browser extensions since 2020, with 70% of those extensions used as adware to target users with advertisements. The most common payloads carried by malicious web browser extensions during the first half of 2022 belonged to adware families, snooping on browsing activity and promoting affiliate links.

Users of Apple's Instagram and Facebook iOS apps are being warned that both use an in-app browser that allows parent company Meta to track 'every single tap' users make with external websites accessed via the software. iOS users' concerns over tracking were addressed by Apple's 2021 release of iOS 14.5 and a feature called App Tracking Transparency.
DuckDuckGo announced today that they will now be blocking all third-party Microsoft tracking scripts in their privacy browser after failing to block them in the past. This change comes after the company faced massive blowback in May for not blocking some third-party Microsoft trackers in the DuckDuckGo browser due to a syndicated search content agreement between the two companies.
DuckDuckGo announced today that they will now be blocking all third-party Microsoft tracking scripts in their privacy browser after failing to block them in the past. This change comes after the company faced massive blowback in May for not blocking some third-party Microsoft trackers in the DuckDuckGo browser due to a syndicated search content agreement between the two companies.
Two universal and seemingly innocuous browser features - the ability to create bookmarks and browser synchronization - make users' lives easier, but may also allow hackers to establish a covert data exfiltration channel. Some attackers have also recently managed to exploit Chrome's syncing feature and use an extension to connect their computer directly to a targeted workstation, creating a covert channel for remote data manipulation, but also for data exfiltration and C&C communication.
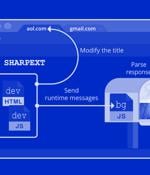
A threat actor operating with interests aligned with North Korea has been deploying a malicious extension on Chromium-based web browsers that's capable of stealing email content from Gmail and AOL. Cybersecurity firm Volexity attributed the malware to an activity cluster it calls SharpTongue, which is said to share overlaps with an adversarial collective publicly referred to under the name Kimsuky. SharpTongue has a history of singling out individuals working for organizations in the U.S., Europe, and South Korea who "Work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea," researchers Paul Rascagneres and Thomas Lancaster said.