Security News

At least six distinct botnet malware operations are hunting for TP-Link Archer AX21 routers vulnerable to a command injection security issue reported and addressed last year. Yesterday, Fortinet issued another warning saying that it observed a surge in the malicious activity exploiting the vulnerability, noting that it originated from six botnet operations.

A Romanian botnet group named 'RUBYCARP' is leveraging known vulnerabilities and performing brute force attacks to breach corporate networks and compromise servers for financial gain. According to a new report by Sysdig, RUBYCARP currently operates a botnet managed via private IRC channels comprising over 600 compromised servers.
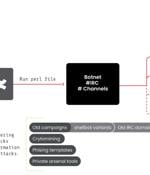
A threat group of suspected Romanian origin called RUBYCARP has been observed maintaining a long-running botnet for carrying out crypto mining, distributed denial-of-service (DDoS), and phishing...

A botnet previously considered to be rendered inert has been observed enslaving end-of-life (EoL) small home/small office (SOHO) routers and IoT devices to fuel a criminal proxy service called...

Authorities from eleven nations have delivered a sequel to the January takedown of a botnet run by Russia on compromised Ubiquiti Edge OS routers - in the form of a warning that Russia may try again, so owners of the devices should take precautions. Moobot allowed GRU and its minions to install and run scripts to build a 1,000-strong botnet, which it used for power phishing, spying, credential harvesting, and data theft.

In January 2024, an operation dismantled a network of hundreds of SOHO routers controlled by GRU Military Unit 26165, also known as APT 28, Sofacy Group, Forest Blizzard, Pawn Storm, Fancy Bear, and Sednit. The Department's court-authorized operation leveraged the Moobot malware to copy and delete stolen and malicious data and files from compromised routers.

The U.S. government on Thursday said it disrupted a botnet comprising hundreds of small office and home office (SOHO) routers in the country that was put to use by the Russia-linked APT28 actor to...

The US government today said it disrupted a botnet that Russia's GRU military intelligence unit used for phishing expeditions, spying, credential harvesting, and data theft against American and foreign governments and other strategic targets. Then the GRU spying team used Moobot to install their own bespoke scripts and files that repurposed the botnet, thus "Turning it into a global cyber espionage platform," according to the Feds.

The FBI took down a botnet of small office/home office routers used by Russia's Main Intelligence Directorate of the General Staff to proxy malicious traffic and to target the United States and its allies in spearphishing and credential theft attacks. This network of hundreds of Ubiquiti Edge OS routers infected with Moobot malware was controlled by GRU Military Unit 26165, also tracked as APT28, Fancy Bear, and Sednit.

The FBI took down a botnet of small office/home office routers used by Russia's Main Intelligence Directorate of the General Staff in spearphishing and credential theft attacks targeting the United States and its allies. Subsequently, the GRU hackers leveraged the Moobot malware to deploy their own custom malicious tools, effectively repurposing the botnet into a cyber espionage tool with global reach.